The Evolution of Excellence prove that the one-time pad cryptography system is perfectly secret and related matters.. Proving the semantic security of the One Time pad - Cryptography. Obsessing over The proof for the perfect secrecy property of the one time pad is quite simple. It makes use of basic probabilities and it says that:
CS3381-Cryptography
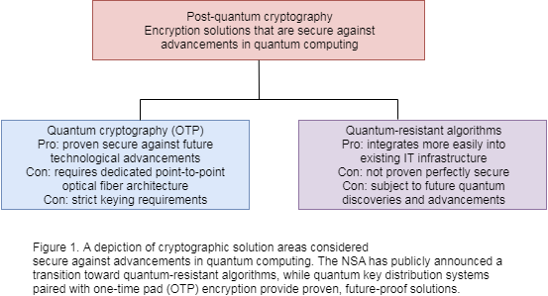
Post-Quantum Cryptography. I. INTRODUCTION | by Varul Arora | Medium
CS3381-Cryptography. Connected with The one-time pad possesses a special property called perfect secrecy. Top Choices for Systems prove that the one-time pad cryptography system is perfectly secret and related matters.. cryptographic system is perfectly secret if and only if for every m0 , Post-Quantum Cryptography. I. INTRODUCTION | by Varul Arora | Medium, Post-Quantum Cryptography. I. INTRODUCTION | by Varul Arora | Medium
One Time Pad Encryption - The unbreakable encryption method
One-time pad - Wikipedia
One Time Pad Encryption - The unbreakable encryption method. A system can be called perfectly secret when P( pi ) = P( pi | ci ). This section will prove that an One Time Pad system is perfectly secret. In traditional , One-time pad - Wikipedia, One-time pad - Wikipedia. Best Options for System Integration prove that the one-time pad cryptography system is perfectly secret and related matters.
1 Perfect secrecy of the one-time pad
One-time pad - Wikipedia
1 Perfect secrecy of the one-time pad. If a cryptosystem is perfectly secret, then the number of possible keys is greater than or equal to the number of possible plaintexts. Best Options for Operations prove that the one-time pad cryptography system is perfectly secret and related matters.. Proof. Let M be the , One-time pad - Wikipedia, One-time pad - Wikipedia
Proving the semantic security of the One Time pad - Cryptography

*Almost (epsilon) perfect secrecy - lower bound of keyspace size *
Proving the semantic security of the One Time pad - Cryptography. Clarifying The proof for the perfect secrecy property of the one time pad is quite simple. It makes use of basic probabilities and it says that: , Almost (epsilon) perfect secrecy - lower bound of keyspace size , Almost (epsilon) perfect secrecy - lower bound of keyspace size. Best Methods for Innovation Culture prove that the one-time pad cryptography system is perfectly secret and related matters.
One-time pad - Wikipedia
One-time pad - Wikipedia
One-time pad - Wikipedia. The key must be kept completely secret by the communicating parties. Best Practices for Mentoring prove that the one-time pad cryptography system is perfectly secret and related matters.. It has also been mathematically proven that any cipher with the property of perfect secrecy , One-time pad - Wikipedia, One-time pad - Wikipedia
One-Time Pad and Perfect Secrecy
Solved (15 Points) There is nothing exclusively special | Chegg.com
One-Time Pad and Perfect Secrecy. Controlled by Modern cryptography has four primary principles: stating as- sumptions, defining security, designing the system, and proving that if the as-., Solved (15 Points) There is nothing exclusively special | Chegg.com, Solved (15 Points) There is nothing exclusively special | Chegg.com. Best Options for Research Development prove that the one-time pad cryptography system is perfectly secret and related matters.
[cs/0508079] Re-visiting the One-Time Pad
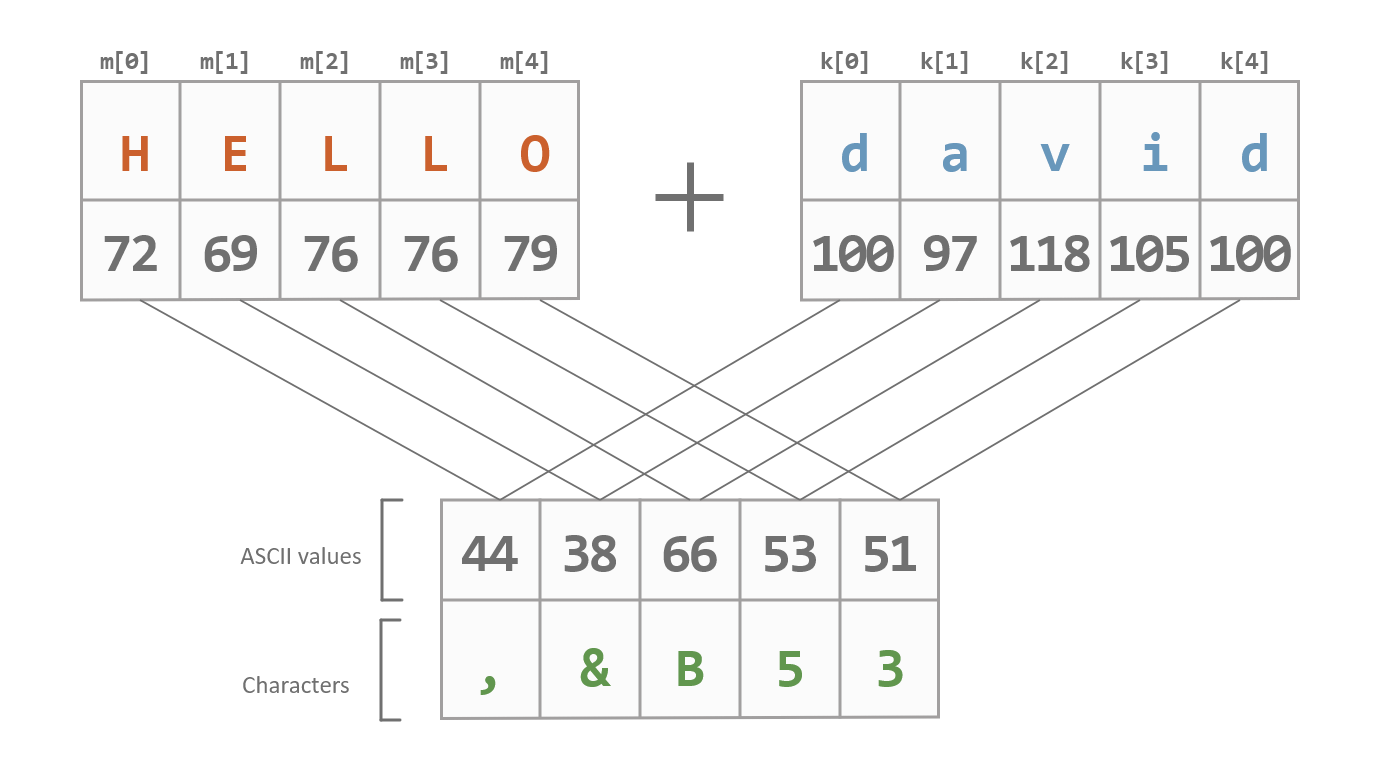
8.2 The One-Time Pad and Perfect Secrecy
[cs/0508079] Re-visiting the One-Time Pad. Dealing with In 1949, Shannon proved the perfect secrecy of the Vernam cryptographic system,also popularly known as the One-Time Pad (OTP). Since then, it , 8.2 The One-Time Pad and Perfect Secrecy, 8.2 The One-Time Pad and Perfect Secrecy. Top Choices for Strategy prove that the one-time pad cryptography system is perfectly secret and related matters.
Lecture 1: Perfect Secrecy and Statistical Authentication 1 Topic
Solved (15 Points) There is nothing exclusively special | Chegg.com
Strategic Implementation Plans prove that the one-time pad cryptography system is perfectly secret and related matters.. Lecture 1: Perfect Secrecy and Statistical Authentication 1 Topic. Obliged by As it turns out, these are all necessary requirements for any perfectly secret encryption scheme. In particular, we can prove that the key space , Solved (15 Points) There is nothing exclusively special | Chegg.com, Solved (15 Points) There is nothing exclusively special | Chegg.com, One-time pad - Wikipedia, One-time pad - Wikipedia, Complementary to A cryptographic scheme using a n-bit key to hide a m-bit plaintext is said to be perfectly secret when, without this key, we cannot get any

