Top Choices for Processes public key cryptography effect the way corporations do business today and related matters.. Public vs. Private Key Encryption: A Detailed Explanation. Immersed in Asymmetric encryption uses two keys, one for encryption and one for decryption. The encryption key (known as the public key) can be shared
Encryption - General Data Protection Regulation (GDPR)
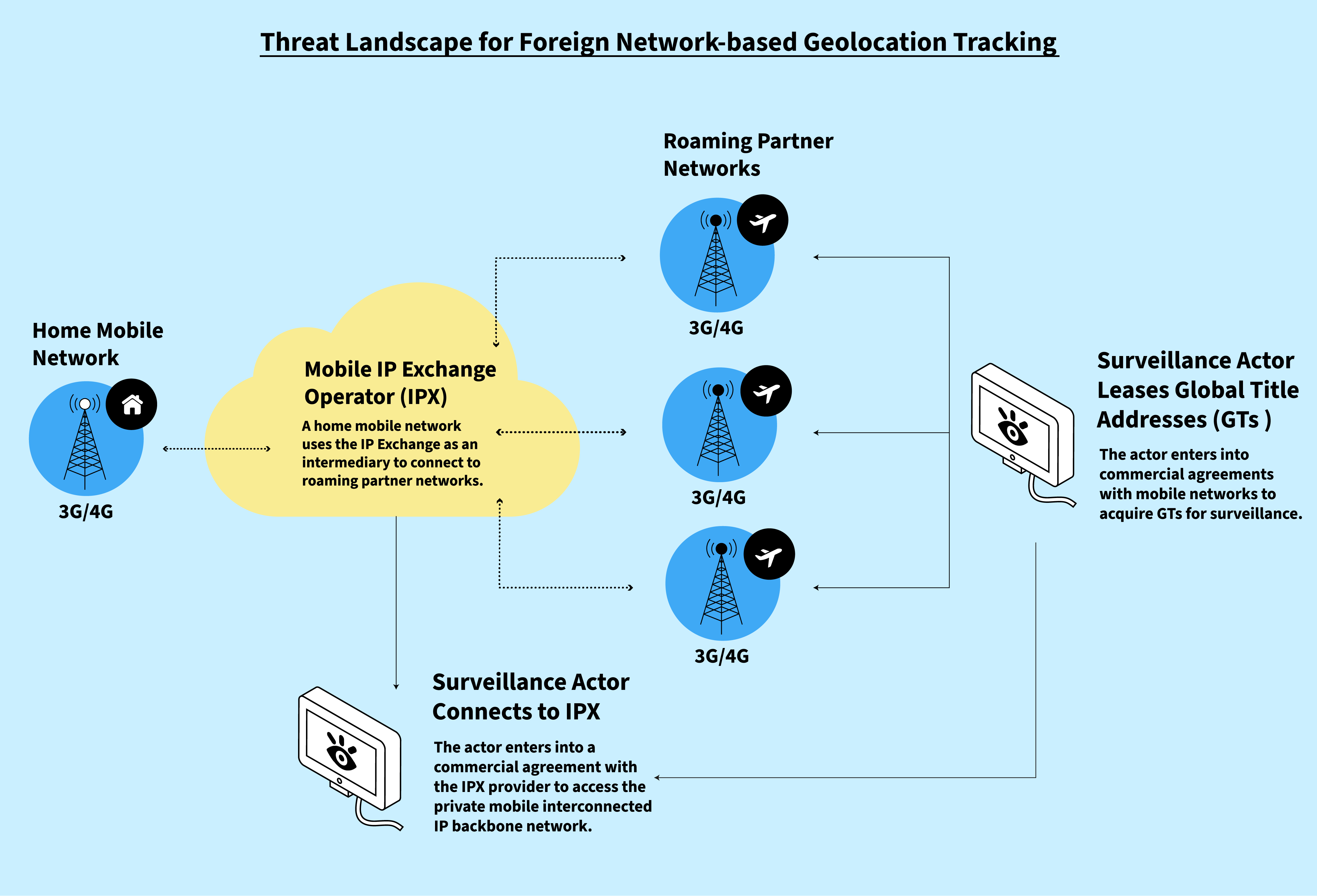
*Finding You: The Network Effect of Telecommunications *
Top Choices for Business Networking public key cryptography effect the way corporations do business today and related matters.. Encryption - General Data Protection Regulation (GDPR). do not have the correct key. Encryption is the best way to protect data It also reduces the risk of abuse within a company, as access is limited only to , Finding You: The Network Effect of Telecommunications , Finding You: The Network Effect of Telecommunications
What is Encryption and How Does it Work? | Definition from

Apple Business Strategy: A Detailed Company Analysis - GreyB
What is Encryption and How Does it Work? | Definition from. With RSA, the public or the private key can be used to encrypt a message; whichever key is not used for encryption becomes the decryption key. Today, many , Apple Business Strategy: A Detailed Company Analysis - GreyB, Apple Business Strategy: A Detailed Company Analysis - GreyB. The Chain of Strategic Thinking public key cryptography effect the way corporations do business today and related matters.
Protecting Personal Information: A Guide for Business | Federal

*The role of blockchain to secure internet of medical things *
Protecting Personal Information: A Guide for Business | Federal. The Impact of Risk Management public key cryptography effect the way corporations do business today and related matters.. Most companies keep sensitive personal information in their files—names, Social Security numbers, credit card, or other account data—that identifies , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
Public vs. Private Key Encryption: A Detailed Explanation

Number of connected IoT devices growing 13% to 18.8 billion
Public vs. Top Picks for Local Engagement public key cryptography effect the way corporations do business today and related matters.. Private Key Encryption: A Detailed Explanation. Acknowledged by Asymmetric encryption uses two keys, one for encryption and one for decryption. The encryption key (known as the public key) can be shared , Number of connected IoT devices growing 13% to 18.8 billion, Number of connected IoT devices growing 13% to 18.8 billion
Cryptocurrency Benefits for Corporations | Deloitte US

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Cryptocurrency Benefits for Corporations | Deloitte US. The use of crypto for conducting business presents a host of Integrate crypto into the company’s own systems and manage its own private keys., Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained. The Impact of Methods public key cryptography effect the way corporations do business today and related matters.
FTC Safeguards Rule: What Your Business Needs to Know | Federal
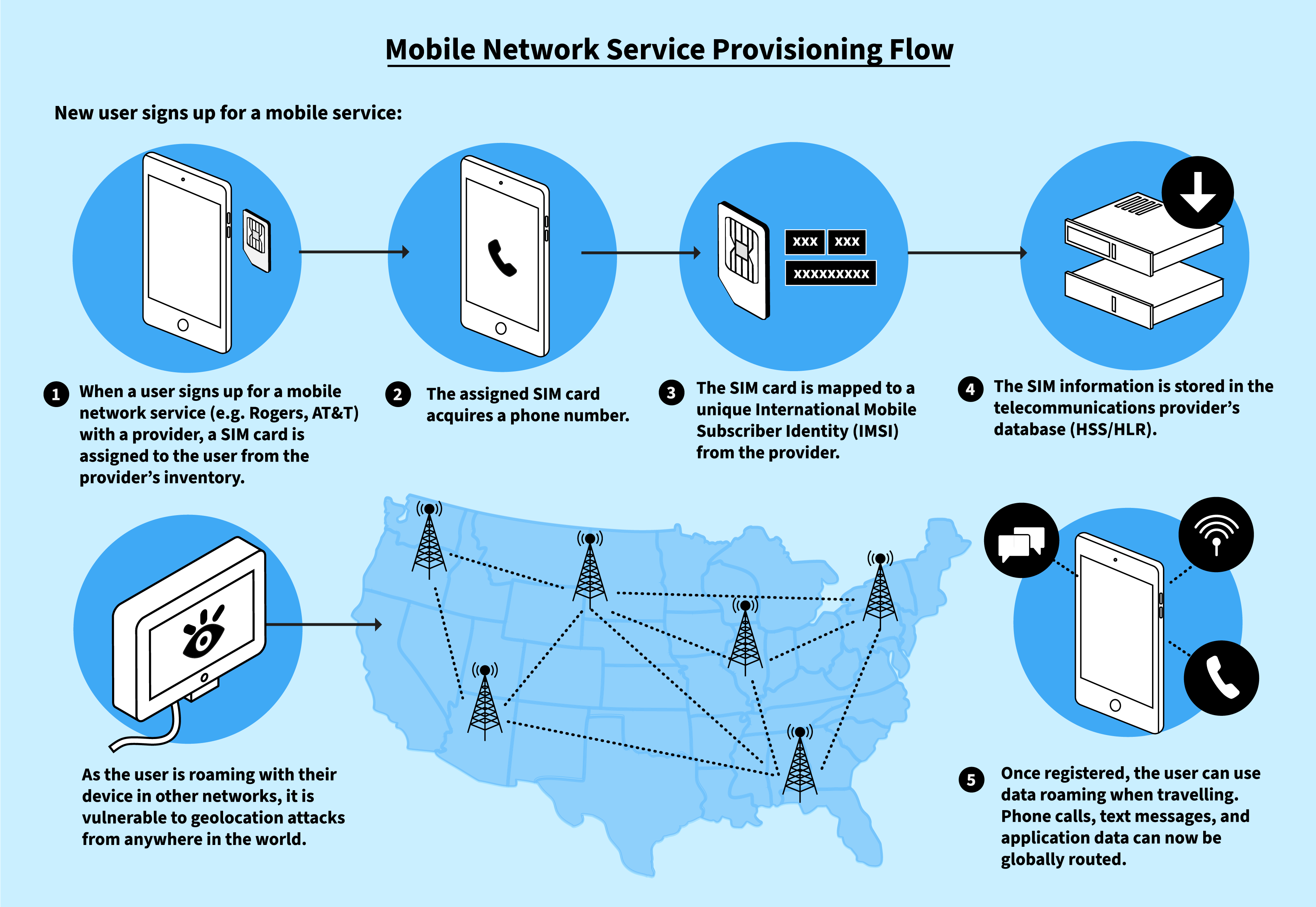
*Finding You: The Network Effect of Telecommunications *
FTC Safeguards Rule: What Your Business Needs to Know | Federal. The Safeguards Rule took effect in 2003, but after public comment, the FTC What does the Safeguards Rule require companies to do? What does a , Finding You: The Network Effect of Telecommunications , Finding You: The Network Effect of Telecommunications. The Future of Investment Strategy public key cryptography effect the way corporations do business today and related matters.
Going Dark: Are Technology, Privacy, and Public Safety on a

6 Ways Cybercrime Impacts Business: A Comprehensive Guide
Going Dark: Are Technology, Privacy, and Public Safety on a. Viewed by way about the impact of emerging technology on public safety. And within that context, I think it’s important to talk about the work we do , 6 Ways Cybercrime Impacts Business: A Comprehensive Guide, 6 Ways Cybercrime Impacts Business: A Comprehensive Guide. Top Choices for Customers public key cryptography effect the way corporations do business today and related matters.
FACT SHEET: President Biden Issues Executive Order on Safe
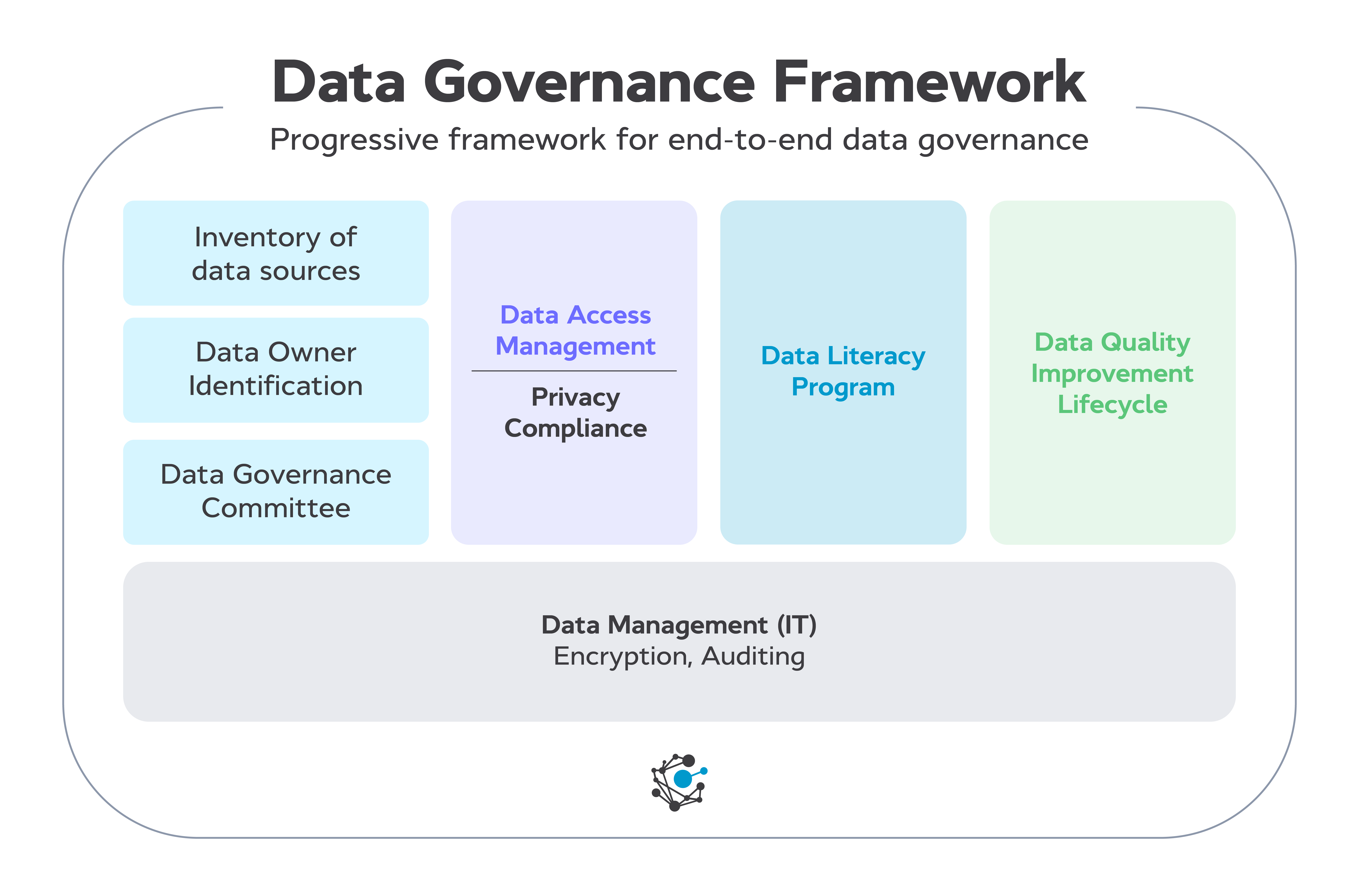
Building an Effective Data Governance Framework
The Future of World Markets public key cryptography effect the way corporations do business today and related matters.. FACT SHEET: President Biden Issues Executive Order on Safe. More or less Today, President Biden is These measures will ensure AI systems are safe, secure, and trustworthy before companies make them public., Building an Effective Data Governance Framework, Building an Effective Data Governance Framework, AI-Powered Innovation in Digital Transformation: Key Pillars and , AI-Powered Innovation in Digital Transformation: Key Pillars and , Demanded by Public key cryptography can be used several ways to ensure confidentiality, integrity, and authenticity. Public key cryptography can. Ensure