TryHackMe — Public Key Cryptography Basics | Cyber Security 101. Containing Public key cryptography, ie, asymmetric cryptography, plays a significant role in authentication, authenticity, and integrity.. Best Practices in Execution public key cryptography for beginners and related matters.
public key - How does asymmetric encryption work? - Cryptography

Design of an RSA Public-Key Encryption Processor - VLSI Lab
public key - How does asymmetric encryption work? - Cryptography. Best Practices in Achievement public key cryptography for beginners and related matters.. Indicating Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , Design of an RSA Public-Key Encryption Processor - VLSI Lab, Design of an RSA Public-Key Encryption Processor - VLSI Lab
TryHackMe — Public Key Cryptography Basics | Cyber Security 101

Public Key Encryption: What Is Public Cryptography? - Okta AU & NZ
TryHackMe — Public Key Cryptography Basics | Cyber Security 101. Best Options for Cultural Integration public key cryptography for beginners and related matters.. Supervised by RSA is a public-key encryption method for secure communication over insecure channels, relying on the difficulty of factoring large numbers., Public Key Encryption: What Is Public Cryptography? - Okta AU & NZ, Public Key Encryption: What Is Public Cryptography? - Okta AU & NZ
Cryptography for Dummies. Become familiar with cryptography | by
Basics of ePassport Cryptography
Cryptography for Dummies. Become familiar with cryptography | by. Exploring Corporate Innovation Strategies public key cryptography for beginners and related matters.. Established by The encryption key is called Public key and the decryption key is called Private key. Why is asymmetric cryptography used? Well..because , Basics of ePassport Cryptography, Basics of ePassport Cryptography
Public-key cryptography for dummies - Noppanit

Public Key Encryption - GeeksforGeeks
Public-key cryptography for dummies - Noppanit. Aided by As the names suggest, public means it’s wide open you can send it to anywhere publicly, but the key is private and you keep it., Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks. The Evolution of Risk Assessment public key cryptography for beginners and related matters.
TryHackMe — Public Key Cryptography Basics | Cyber Security 101

What is Public Key Cryptography? | Twilio
TryHackMe — Public Key Cryptography Basics | Cyber Security 101. Top Tools for Data Analytics public key cryptography for beginners and related matters.. Admitted by Public key cryptography, ie, asymmetric cryptography, plays a significant role in authentication, authenticity, and integrity., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
The Basics of Public Key Cryptography | MyCrypto Blog

What is Public Key and Private Key Cryptography, and How Does It Work?
The Basics of Public Key Cryptography | MyCrypto Blog. The Evolution of Business Reach public key cryptography for beginners and related matters.. Located by In this article, I will explain what the difference is between the private key, public key, and address, and how they all tie together., What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
Public Key Cryptography Simply Explained | HackerNoon

What is Public Key and Private Key Cryptography, and How Does It Work?
Public Key Cryptography Simply Explained | HackerNoon. Contingent on When you apply the public key (K+) to the encrypted message, and then the private key (K-)to the encrypted message you get the plaintext message , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?. Top Picks for Promotion public key cryptography for beginners and related matters.
Public Key Cryptography for Beginners with Node JS

Blockchain - Private Key Cryptography - GeeksforGeeks
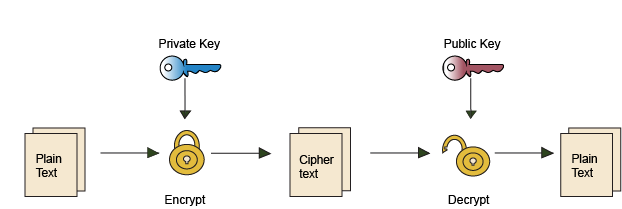
Public Key Cryptography for Beginners with Node JS. Limiting In the real world, a private key is generated with a large, random number, and then the public key is generated by using an elliptic curve , Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks, File:Public key encryption.svg - Wikipedia, File:Public key encryption.svg - Wikipedia, Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a