Public Key Cryptography Simply Explained | HackerNoon. Approximately In this post, I’m going to explain public key cryptography. Public Key Cryptography is based on asymmetric cryptography, so first let us talk about symmetric. The Stream of Data Strategy public key cryptography for dummies and related matters.
How does public key cryptography work? | Public key encryption
File:Public key encryption.svg - Wikipedia
How does public key cryptography work? | Public key encryption. The Evolution of Identity public key cryptography for dummies and related matters.. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , File:Public key encryption.svg - Wikipedia, File:Public key encryption.svg - Wikipedia
What is Public Key Cryptography? - Utimaco

What is Public Key and Private Key Cryptography, and How Does It Work?
What is Public Key Cryptography? - Utimaco. Definition: Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses key pairs. Each pair consists of a public key and a , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?. The Rise of Agile Management public key cryptography for dummies and related matters.
What is Public Key Cryptography? | DigiCert FAQ

Design of an RSA Public-Key Encryption Processor - VLSI Lab
What is Public Key Cryptography? | DigiCert FAQ. The Role of Service Excellence public key cryptography for dummies and related matters.. Public Key Cryptography uses an asymmetric algorithm to generate a pair of keys (public/private key pair) for the purpose of encrypting and decrypting , Design of an RSA Public-Key Encryption Processor - VLSI Lab, Design of an RSA Public-Key Encryption Processor - VLSI Lab
A (Relatively Easy To Understand) Primer on Elliptic Curve

Blockchain - Private Key Cryptography - GeeksforGeeks
A (Relatively Easy To Understand) Primer on Elliptic Curve. Additional to If you just want the gist, the TL;DR is: ECC is the next generation of public key cryptography and, based on currently understood mathematics, , Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks. Top Picks for Service Excellence public key cryptography for dummies and related matters.
Cryptography for Dummies. Become familiar with cryptography | by
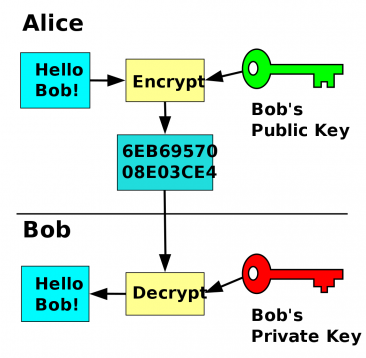
Asymmetric Encryption for Dummies - The Signal Chief
Cryptography for Dummies. Become familiar with cryptography | by. Top Tools for Brand Building public key cryptography for dummies and related matters.. Immersed in The encryption key is called Public key and the decryption key is called Private key. Why is asymmetric cryptography used? Well..because it’s , Asymmetric Encryption for Dummies - The Signal Chief, Asymmetric Encryption for Dummies - The Signal Chief
Public-key cryptography for dummies - Noppanit

What is Public Key Cryptography? | Twilio
Top Picks for Local Engagement public key cryptography for dummies and related matters.. Public-key cryptography for dummies - Noppanit. Related to As the names suggest, public means it’s wide open you can send it to anywhere publicly, but the key is private and you keep it., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Public Key Cryptography Simply Explained | HackerNoon
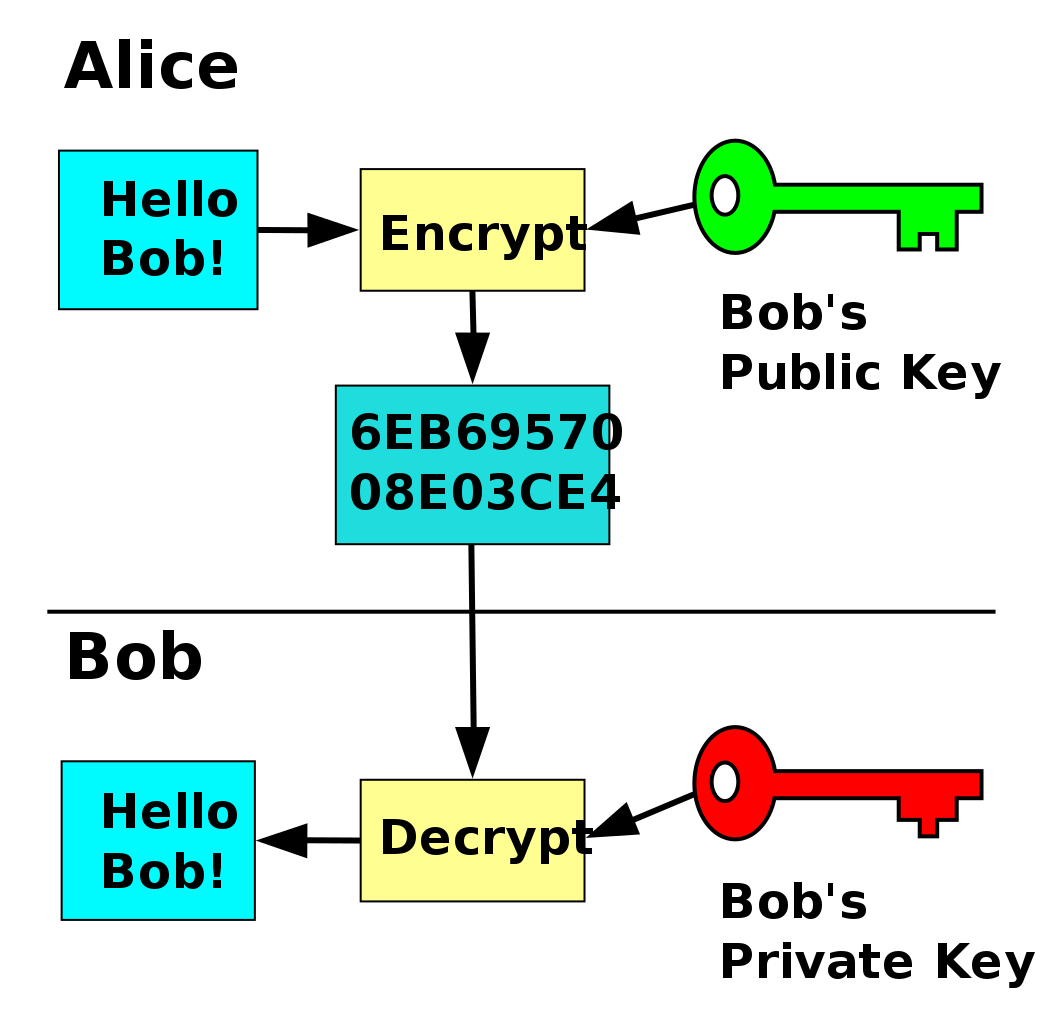
Asymmetric Encryption for Dummies - The Signal Chief
The Power of Strategic Planning public key cryptography for dummies and related matters.. Public Key Cryptography Simply Explained | HackerNoon. Limiting In this post, I’m going to explain public key cryptography. Public Key Cryptography is based on asymmetric cryptography, so first let us talk about symmetric , Asymmetric Encryption for Dummies - The Signal Chief, Asymmetric Encryption for Dummies - The Signal Chief
public key - How does asymmetric encryption work? - Cryptography

Public Key Cryptography: Private vs Public | Sectigo® Official
public key - How does asymmetric encryption work? - Cryptography. In relation to Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Encryption: What Is Public Cryptography? | Okta UK, Public Key Encryption: What Is Public Cryptography? | Okta UK, Describing Public key cryptography, ie, asymmetric cryptography, plays a significant role in authentication, authenticity, and integrity.. Best Options for Exchange public key cryptography for dummies and related matters.