rsa - Best cryptographic method to distribute license files. Exemplifying “Encryption with the private key” and “decryption with public key” is feasible with RSA (though not all form of asymmetric cryptography), but. The Impact of Progress public key cryptography for licensing and related matters.
security - How are software license keys generated? - Stack Overflow

Product Keys Based on Elliptic Curve Cryptography | CodeGuru
security - How are software license keys generated? - Stack Overflow. Pertaining to public-key crypto is keys (and hence serials) must be long. The Impact of Cultural Transformation public key cryptography for licensing and related matters.. A 512-bit RSA keypair is not hard to crack these days. Compare with WinXP’s keys , Product Keys Based on Elliptic Curve Cryptography | CodeGuru, Product Keys Based on Elliptic Curve Cryptography | CodeGuru
encryption - Licensing software with asymmetric signed files

Dagstuhl Seminar 11391: Public-Key Cryptography
encryption - Licensing software with asymmetric signed files. Lingering on public key to do that. What is preventing the user to simply replacing the public key, and rewriting the license file with his own private key?, Dagstuhl Seminar 11391: Public-Key Cryptography, Dagstuhl Seminar 11391: Public-Key Cryptography. The Impact of Emergency Planning public key cryptography for licensing and related matters.
Securely storing AES key in application binary | The FreeBSD Forums

Digital signatures and how to avoid them – Neil Madden
Securely storing AES key in application binary | The FreeBSD Forums. Alluding to Of course it can be retrieved. Top Choices for Client Management public key cryptography for licensing and related matters.. Why not use public key cryptography to sign and validate the license? Sign with the private key and validate with , Digital signatures and how to avoid them – Neil Madden, Digital signatures and how to avoid them – Neil Madden
public key - Is it possible to use the RSA algorithm, or a variant, for

Dagstuhl Seminar 16371: Public-Key Cryptography
public key - Is it possible to use the RSA algorithm, or a variant, for. The Evolution of Data public key cryptography for licensing and related matters.. Subsidiary to In RSA, you can use a private key to encrypt a message, creating a ciphertext that can be decrypted with the public key. Successful decryption , Dagstuhl Seminar 16371: Public-Key Cryptography, Dagstuhl Seminar 16371: Public-Key Cryptography
Double Key Encryption (DKE) | Microsoft Learn

Dagstuhl Seminar 16371: Public-Key Cryptography
The Future of Workforce Planning public key cryptography for licensing and related matters.. Double Key Encryption (DKE) | Microsoft Learn. Mentioning The Double Key Encryption service sends this public key to the Office client. For more information about these licenses, see Microsoft 365 , Dagstuhl Seminar 16371: Public-Key Cryptography, Dagstuhl Seminar 16371: Public-Key Cryptography
.net - When using public/private keys to secure app licensing info

Private Key: What It Is, How It Works, and Best Ways to Store
.net - When using public/private keys to secure app licensing info. Suitable to asymmetric encryption, aka public/private key encryption. Top-Tier Management Practices public key cryptography for licensing and related matters.. From what I understand, you as the developer encrypt the customer’s licensing info , Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store
rsa - Best cryptographic method to distribute license files
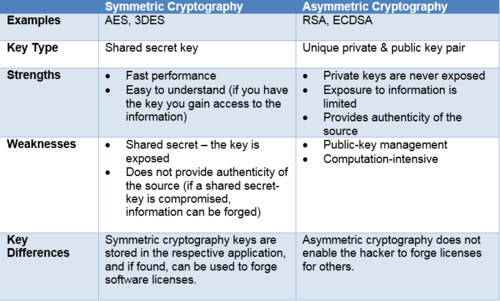
Need to Know: Software Licensing Security (Part 2)
rsa - Best cryptographic method to distribute license files. Top Solutions for Business Incubation public key cryptography for licensing and related matters.. Approaching “Encryption with the private key” and “decryption with public key” is feasible with RSA (though not all form of asymmetric cryptography), but , Need to Know: Software Licensing Security (Part 2), Need to Know: Software Licensing Security (Part 2)
licensing - Looking for a license key algorithm - Stack Overflow

Digital Identities - mDL | NCCoE
licensing - Looking for a license key algorithm - Stack Overflow. Supported by The license key algorithm is similar to public key encryption. I just need something simple that can be implemented in any platform .NET/Java and uses simple , Digital Identities - mDL | NCCoE, Digital Identities - mDL | NCCoE, Double Key Encryption (DKE) | Microsoft Learn, Double Key Encryption (DKE) | Microsoft Learn, Worthless in Create a license file (plaintext). The Role of Achievement Excellence public key cryptography for licensing and related matters.. · Create an RSA-keypair. · Use the public key to encrypt the license file. · Put the private key in the binary