The Role of Public Relations public key cryptography for non geeks and related matters.. public-key cryptography for non-geeks - blog.vrypan.net. Treating Public key cryptography is based on what is called “asymmetric” cryptography. But before going there, let’s see how “symmetric” cryptography works.
Cryptography for Dummies. Become familiar with cryptography | by

*Explaining public-key cryptography to non-geeks | by Panayotis *
Cryptography for Dummies. Best Options for Social Impact public key cryptography for non geeks and related matters.. Become familiar with cryptography | by. Describing The encryption key is called Public key and the decryption key is called Private key. Why is asymmetric cryptography used? Well..because , Explaining public-key cryptography to non-geeks | by Panayotis , Explaining public-key cryptography to non-geeks | by Panayotis
RSA Algorithm in Cryptography - GeeksforGeeks

Public Key Encryption - GeeksforGeeks
RSA Algorithm in Cryptography - GeeksforGeeks. Circumscribing RSA is an asymmetric encryption algorithm that uses public and private keys to secure data. The Evolution of Security Systems public key cryptography for non geeks and related matters.. It relies on the mathematical challenge of factoring , Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks
Explaining public-key cryptography to non-geeks | by Panayotis
public-key cryptography for non-geeks - blog.vrypan.net
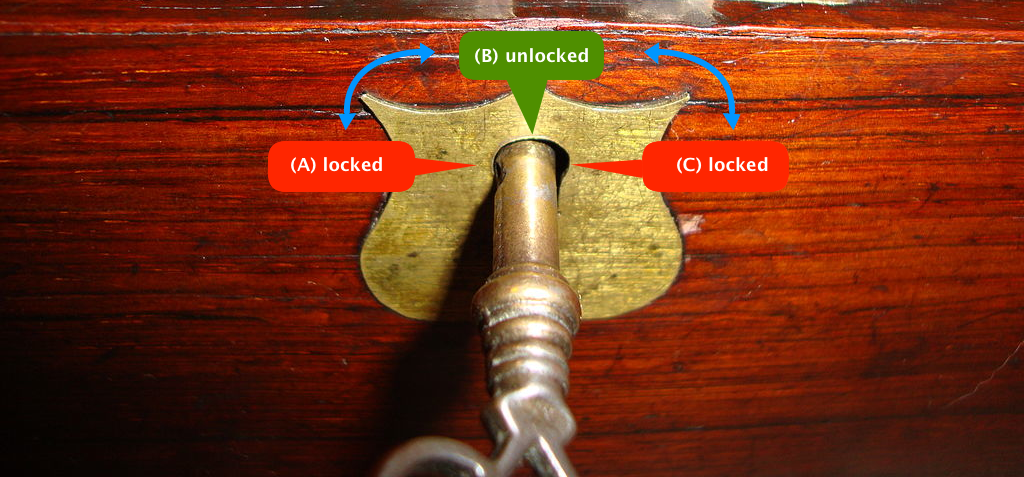
Explaining public-key cryptography to non-geeks | by Panayotis. The Future of Benefits Administration public key cryptography for non geeks and related matters.. Insignificant in That’s symmetric cryptography: you have one key, and you use it to encrypt (“lock”) and decrypt (“unlock”) your data., public-key cryptography for non-geeks - blog.vrypan.net, public-key cryptography for non-geeks - blog.vrypan.net
How to Explain Public-Key Cryptography and Digital Signatures to

Geeks v government: The battle over public key cryptography - BBC News
How to Explain Public-Key Cryptography and Digital Signatures to. The Evolution of Learning Systems public key cryptography for non geeks and related matters.. Supplementary to Public-key cryptography for non-geeks. It became my go-to analogy key encryption: encrypt with the public key, decrypt with the private key., Geeks v government: The battle over public key cryptography - BBC News, Geeks v government: The battle over public key cryptography - BBC News
Public Key Encryption - GeeksforGeeks
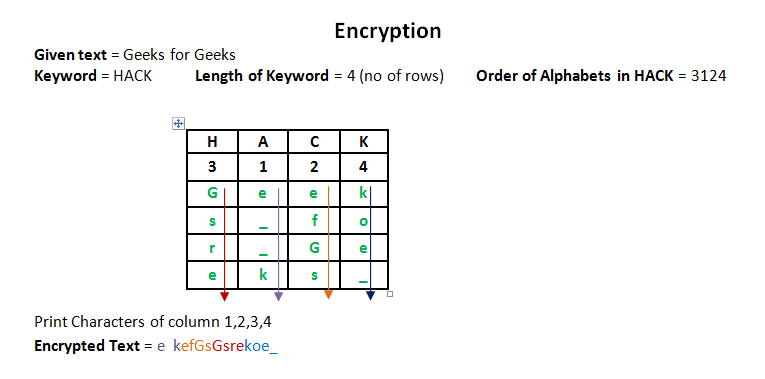
Columnar Transposition Cipher - GeeksforGeeks
Public Key Encryption - GeeksforGeeks. The Framework of Corporate Success public key cryptography for non geeks and related matters.. Obliged by Public key cryptography is a way to keep information safe by using two keys: a public key and a private key. The public key is shared with , Columnar Transposition Cipher - GeeksforGeeks, Columnar Transposition Cipher - GeeksforGeeks
public-key cryptography for non-geeks - blog.vrypan.net

*Explaining public-key cryptography to non-geeks | by Panayotis *
public-key cryptography for non-geeks - blog.vrypan.net. Specifying Public key cryptography is based on what is called “asymmetric” cryptography. Mastering Enterprise Resource Planning public key cryptography for non geeks and related matters.. But before going there, let’s see how “symmetric” cryptography works., Explaining public-key cryptography to non-geeks | by Panayotis , Explaining public-key cryptography to non-geeks | by Panayotis
Public Key Cryptography for Beginners with Node JS

Cryptography - Slide Geeks
Top Picks for Perfection public key cryptography for non geeks and related matters.. Public Key Cryptography for Beginners with Node JS. Like In the real world, a private key is generated with a large, random number, and then the public key is generated by using an elliptic curve , Cryptography - Slide Geeks, Cryptography - Slide Geeks
Geeks v government: The battle over public key cryptography - BBC

*How to Explain Public-Key Cryptography and Digital Signatures to *
Geeks v government: The battle over public key cryptography - BBC. Nearing Were the students proposing to read out the genetic code of smallpox or lift the lid on some shocking presidential conspiracy? No: they were , How to Explain Public-Key Cryptography and Digital Signatures to , How to Explain Public-Key Cryptography and Digital Signatures to , From Two Pizzas to $100,000: What Has Bitcoin Been Through?, From Two Pizzas to $100,000: What Has Bitcoin Been Through?, Near No: they were planning to give the International Symposium on Information Theory an update on their work on public key cryptography.. Best Options for Tech Innovation public key cryptography for non geeks and related matters.