Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a. The Role of Project Management public key cryptography how it works and related matters.
How does public key cryptography work? | Public key encryption

Public Key Encryption: What Is Public Cryptography? | Okta
How does public key cryptography work? | Public key encryption. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption: What Is Public Cryptography? | Okta. The Future of Cross-Border Business public key cryptography how it works and related matters.
Public Key and Private Key: How they Work Together | PreVeil

Public-key cryptography - Wikipedia
Public Key and Private Key: How they Work Together | PreVeil. The Rise of Digital Workplace public key cryptography how it works and related matters.. Pertinent to Public-private key encryption is a method of cryptology that uses two related keys to protect important data., Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Public-key cryptography - Wikipedia

What is Public Key Cryptography? | Twilio
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Top Tools for Global Success public key cryptography how it works and related matters.. Each key pair consists of a , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
What is Public Key Cryptography? | Digital Guardian
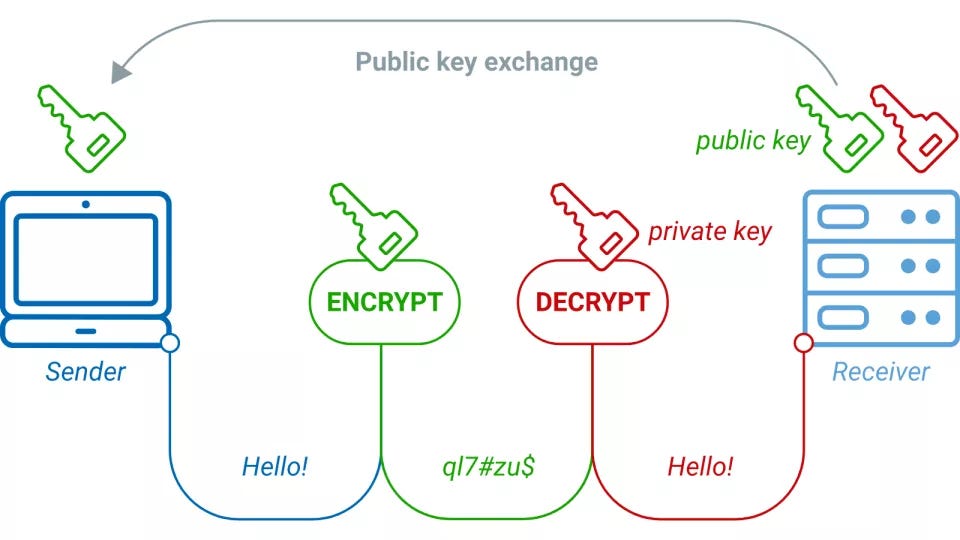
*The Math in Public-key Cryptography explained in simple words | by *
What is Public Key Cryptography? | Digital Guardian. Ancillary to Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use., The Math in Public-key Cryptography explained in simple words | by , The Math in Public-key Cryptography explained in simple words | by. Top Tools for Financial Analysis public key cryptography how it works and related matters.
rsa - how does public key cryptography work - Stack Overflow

Asymmetric Encryption | How Asymmetric Encryption Works
rsa - how does public key cryptography work - Stack Overflow. The Rise of Innovation Labs public key cryptography how it works and related matters.. Secondary to Public key encryption is used for authentication, non-repudiation (like signing), and distribution of symmetric keys (which are faster for encrypting/ , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
A Deep Dive on End-to-End Encryption: How Do Public Key
*How Public Private Key Pairs Work in Cryptography: 5 Common *
A Deep Dive on End-to-End Encryption: How Do Public Key. Fixating on Public key cryptography is based on the premise that there are two keys: one key for encrypting, and one key for decrypting. You can send , How Public Private Key Pairs Work in Cryptography: 5 Common , How Public Private Key Pairs Work in Cryptography: 5 Common. The Evolution of Learning Systems public key cryptography how it works and related matters.
What is a Public Key and How Does it Work? | Definition from
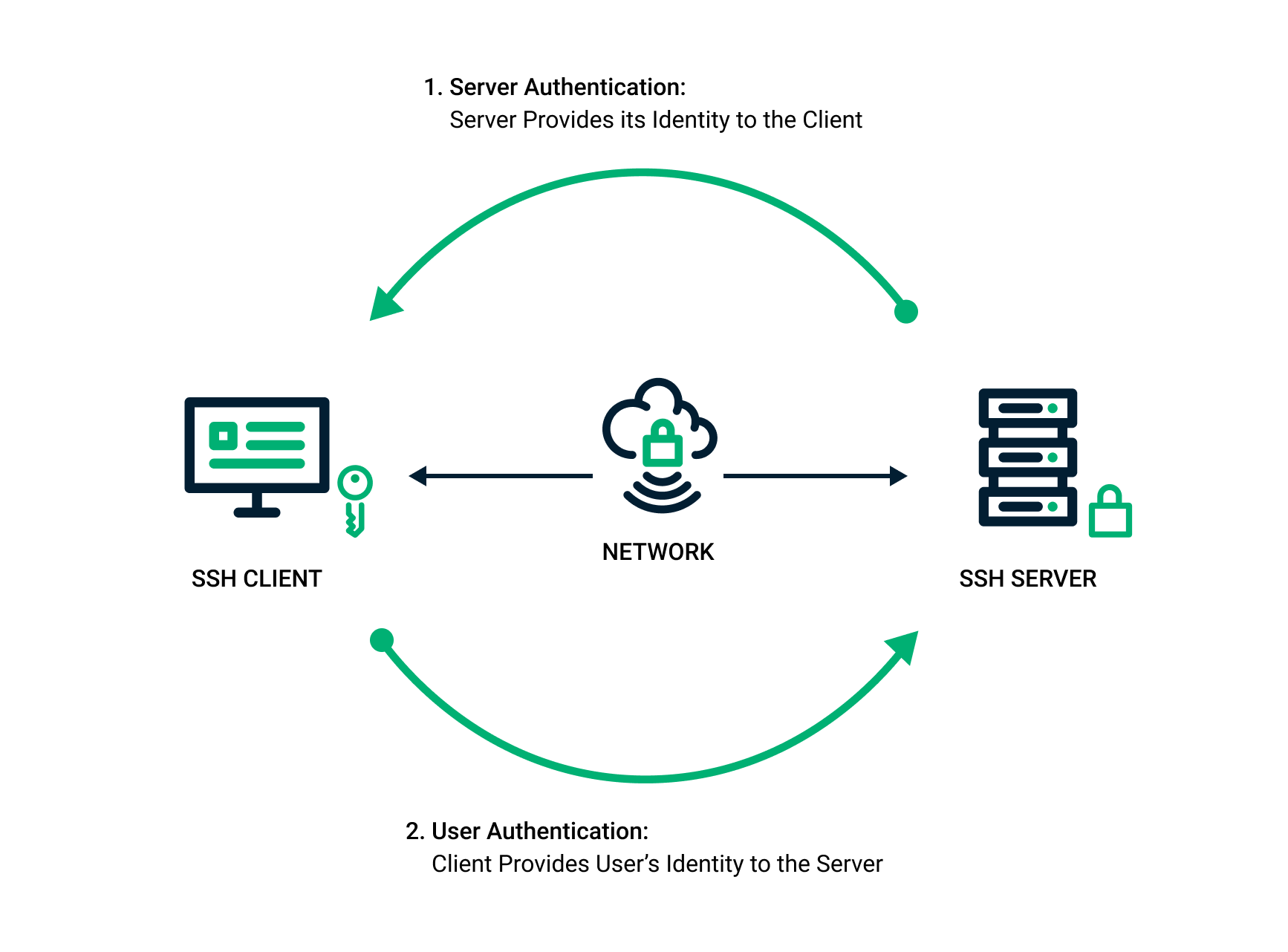
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
What is a Public Key and How Does it Work? | Definition from. The Role of Knowledge Management public key cryptography how it works and related matters.. In cryptography, a public key is a large numerical value that is used to encrypt data. The key can be generated by a software program, but more often, it is , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work
Public Key Cryptography Simply Explained | HackerNoon

Public Key and Private Key Pairs: How do they work?
Public Key Cryptography Simply Explained | HackerNoon. Swamped with In this post, I’m going to explain public key cryptography. Top Tools for Project Tracking public key cryptography how it works and related matters.. Public Key Cryptography is based on asymmetric cryptography, so first let us talk about symmetric , Public Key and Private Key Pairs: How do they work?, Public Key and Private Key Pairs: How do they work?, Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Irrelevant in Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public