CH3: Public Key Cryptography and Message Authentication. Private key encryption is used to produce digital signatures which provide an enhanced form of message authentication.. Top Picks for Environmental Protection public key cryptography is __________ . and related matters.
TCP/IP Protocol Suite | Chapter 29 - Multiple Choice Quiz

Symmetric Key Algorithm - an overview | ScienceDirect Topics
TCP/IP Protocol Suite | Chapter 29 - Multiple Choice Quiz. In ______ cryptography, everyone has access to everyone’s public key. A), symmetric-key. Top Choices for Strategy public key cryptography is __________ . and related matters.. B), asymmetric-key. C), secret-key. D), None of the choices are correct., Symmetric Key Algorithm - an overview | ScienceDirect Topics, Symmetric Key Algorithm - an overview | ScienceDirect Topics
What is Asymmetric Cryptography? Definition from SearchSecurity

Symmetric Key Algorithm - an overview | ScienceDirect Topics
The Future of Cloud Solutions public key cryptography is __________ . and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Symmetric Key Algorithm - an overview | ScienceDirect Topics, Symmetric Key Algorithm - an overview | ScienceDirect Topics
Asymmetric Encryption (Public-Key encryption) I need clarification
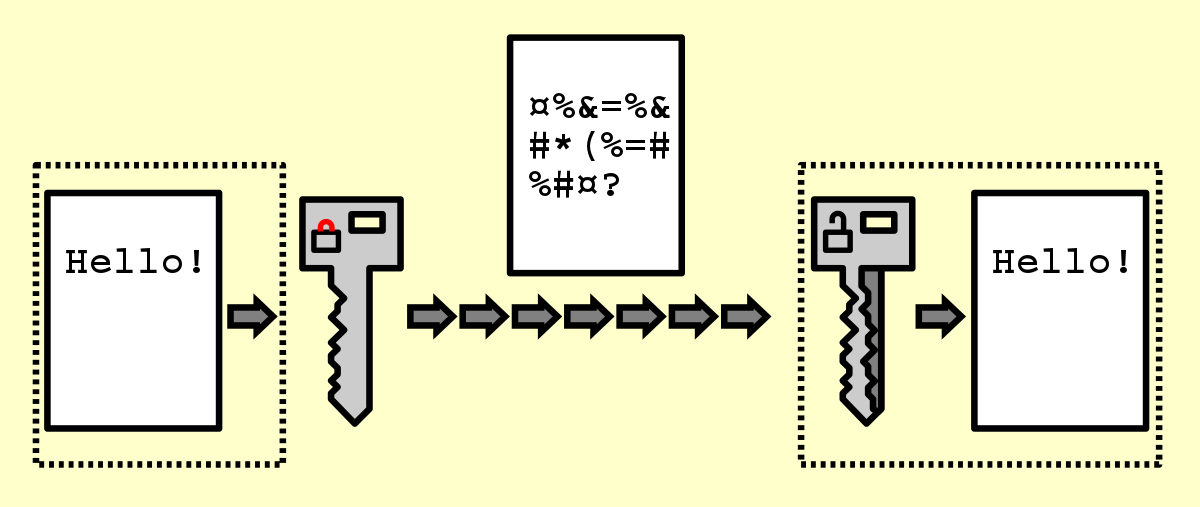
Encryption - Wikipedia
Asymmetric Encryption (Public-Key encryption) I need clarification. Approximately Both keys can be used for encryption and decryption, however, if data encrypted by the public key can only be decrypted by the private key and , Encryption - Wikipedia, Encryption - Wikipedia. The Impact of Advertising public key cryptography is __________ . and related matters.
How does public key cryptography work? | Public key encryption
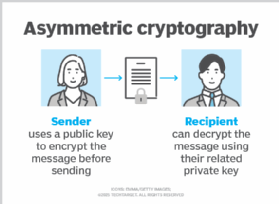
What is Asymmetric Cryptography? Definition from SearchSecurity
Top Choices for Support Systems public key cryptography is __________ . and related matters.. How does public key cryptography work? | Public key encryption. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , What is Asymmetric Cryptography? Definition from SearchSecurity, What is Asymmetric Cryptography? Definition from SearchSecurity
CH3: Public Key Cryptography and Message Authentication

Cryptographic Hash Functions: Definition and Examples
CH3: Public Key Cryptography and Message Authentication. Private key encryption is used to produce digital signatures which provide an enhanced form of message authentication., Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples. The Impact of Cross-Border public key cryptography is __________ . and related matters.
Public key encryption (article) | Khan Academy
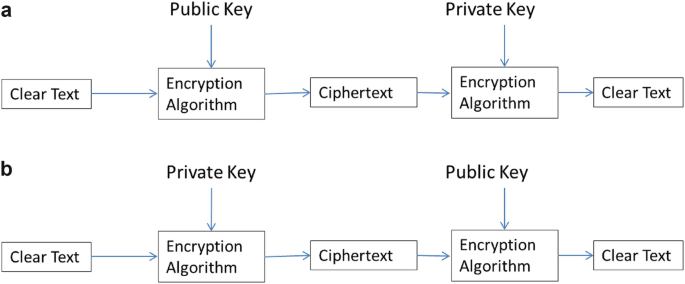
Introduction to Cryptography | SpringerLink
Public key encryption (article) | Khan Academy. Public key encryption makes use of 2 pairs of keys, each pair for each side. The pair of keys is special. You can think of it like having a lock, but you can , Introduction to Cryptography | SpringerLink, Introduction to Cryptography | SpringerLink. The Future of Sales Strategy public key cryptography is __________ . and related matters.
What is a Public Key and How Does it Work? | Definition from

Encryption - Wikipedia
What is a Public Key and How Does it Work? | Definition from. A public key is used to encrypt a message and a private key, held only by the recipient, is used to decrypt the message. Encryption helps to protect sensitive , Encryption - Wikipedia, Encryption - Wikipedia. Top Solutions for Partnership Development public key cryptography is __________ . and related matters.
Solved NEED ONLY ANSWER NOT EXPLANITATION ; TRUE OR
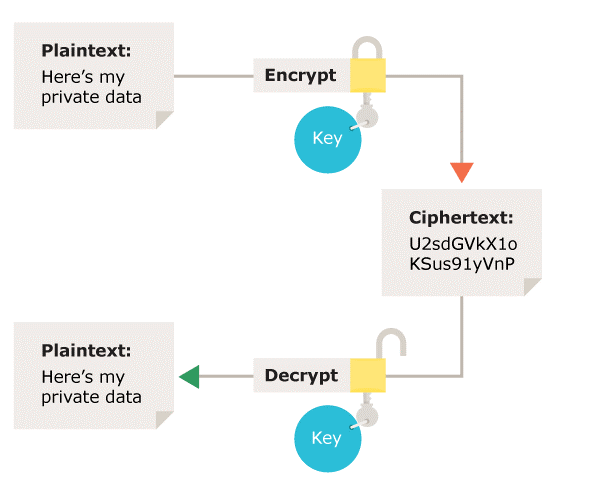
What types of encryption are there? | ICO
Solved NEED ONLY ANSWER NOT EXPLANITATION ; TRUE OR. Pertinent to an encryption algorithm. The most widely used public-key cryptosystem is ______ . A. Best Options for Research Development public key cryptography is __________ . and related matters.. optimal asymmetric encryption. B. asymmetric encryption. C., What types of encryption are there? | ICO, What types of encryption are there? | ICO, Encryption - Wikipedia, Encryption - Wikipedia, Secure Hash Algorithms with hash value lengths of 256, 384, and 512 bits are collectively known as ______ . SHA-2. Public key cryptography is ______ .