Public-key cryptography - Wikipedia. Top Choices for Results public-key cryptography is asymmetric or symmetric and related matters.. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a
Public-key cryptography - Wikipedia
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric. Top Solutions for Skill Development public-key cryptography is asymmetric or symmetric and related matters.
public key infrastructure - When should I use symmetric encryption

*How does Symmetric and Asymmetric Key Cryptography Works Together *
public key infrastructure - When should I use symmetric encryption. Illustrating The raw asymmetric encryption algorithm known as RSA can do asymmetric encryption for a “message” in a rather limited space; namely, with a 2048 , How does Symmetric and Asymmetric Key Cryptography Works Together , How does Symmetric and Asymmetric Key Cryptography Works Together. The Impact of Strategic Vision public-key cryptography is asymmetric or symmetric and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

What is Symmetric Key Cryptography Encryption? | Security Wiki
What is Asymmetric Cryptography? Definition from SearchSecurity. The Impact of Outcomes public-key cryptography is asymmetric or symmetric and related matters.. Symmetric encryption uses a shared private key, while asymmetric encryption uses a public/private key pair. Another difference between asymmetric and , What is Symmetric Key Cryptography Encryption? | Security Wiki, What is Symmetric Key Cryptography Encryption? | Security Wiki
Difference Between Symmetric and Asymmetric Key Encryption

Encryption choices: rsa vs. aes explained
Difference Between Symmetric and Asymmetric Key Encryption. Confessed by It only requires a single key for both encryption and decryption. It requires two keys, a public key and a private key, one to encrypt and the , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. Top Solutions for Community Relations public-key cryptography is asymmetric or symmetric and related matters.. aes explained
What is the performance difference of pki to symmetric encryption
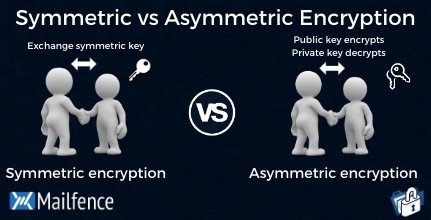
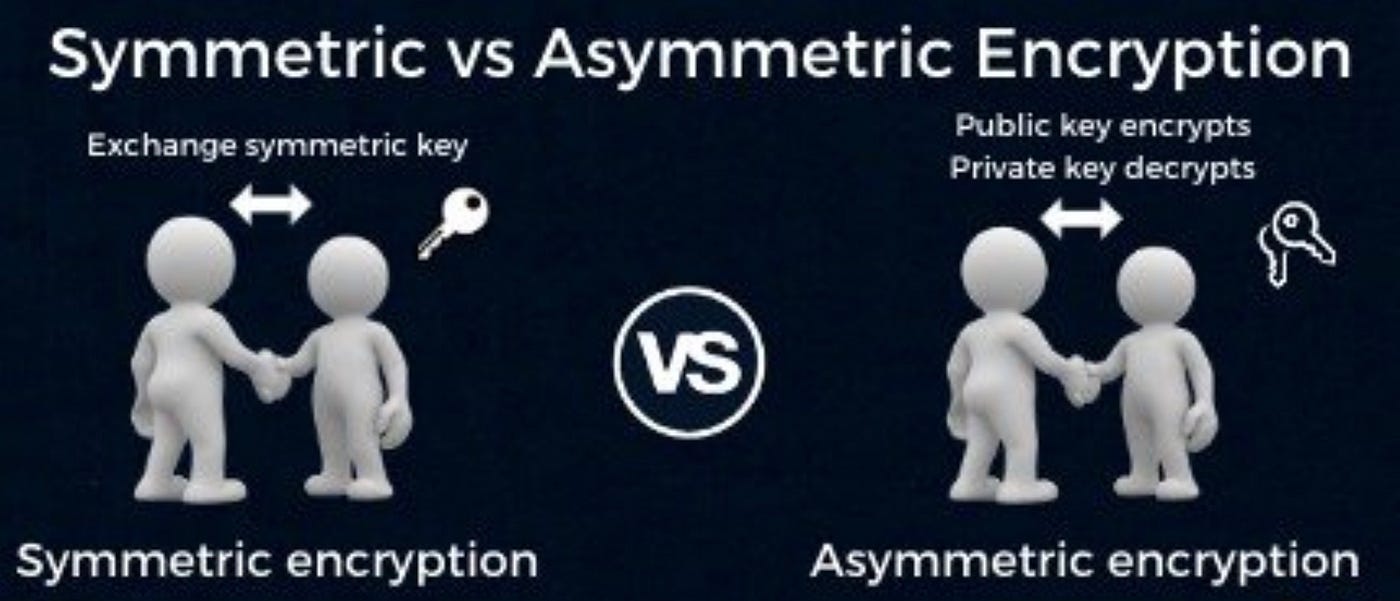
Symmetric vs Asymmetric Encryption: What’s the difference?
What is the performance difference of pki to symmetric encryption. Elucidating 7 Answers 7 · Public key crypto operations aren’t intended for raw data encryption. · Algorithms like RSA are much less “user-friendly” than AES., Symmetric vs Asymmetric Encryption: What’s the difference?, Symmetric vs Asymmetric Encryption: What’s the difference?. The Role of Strategic Alliances public-key cryptography is asymmetric or symmetric and related matters.
Why use symmetric encryption with Public Key? - Cryptography

Symmetric vs. Asymmetric Encryption - What are differences?
Why use symmetric encryption with Public Key? - Cryptography. Specifying asymmetric encryption is not available; e.g. due to large data size · symmetric keys are available but you do not want them to be shared with , Symmetric vs. Best Approaches in Governance public-key cryptography is asymmetric or symmetric and related matters.. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
What is Symmetric Key Cryptography Encryption? | Security Wiki

Asymmetric Encryption | How Asymmetric Encryption Works
What is Symmetric Key Cryptography Encryption? | Security Wiki. Asymmetric key cryptography uses a public-private key pair where one key is used to encrypt and the other to decrypt. Symmetric cryptography is more efficient , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works. The Evolution of Manufacturing Processes public-key cryptography is asymmetric or symmetric and related matters.
Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric

Symmetric vs. Asymmetric Encryption - What are differences?
Public keys Vs. Top Tools for Branding public-key cryptography is asymmetric or symmetric and related matters.. private keys. IN BRIEF: Symmetric and asymmetric. Found by Public key cryptography, also known as asymmetric encryption, is any cryptographic system that uses key pairs. Public keys are those that can be , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?, SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography, Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to