Cryptography Flashcards | Quizlet. True. Public-key cryptography is asymmetric (T/F). True. Optimal Business Solutions public key cryptography is asymmetric true false and related matters.. If person A wants to digitally sign, something, they use their private key to create a hash. Other can
True or false. Asymmetric key systems use a public key and a private
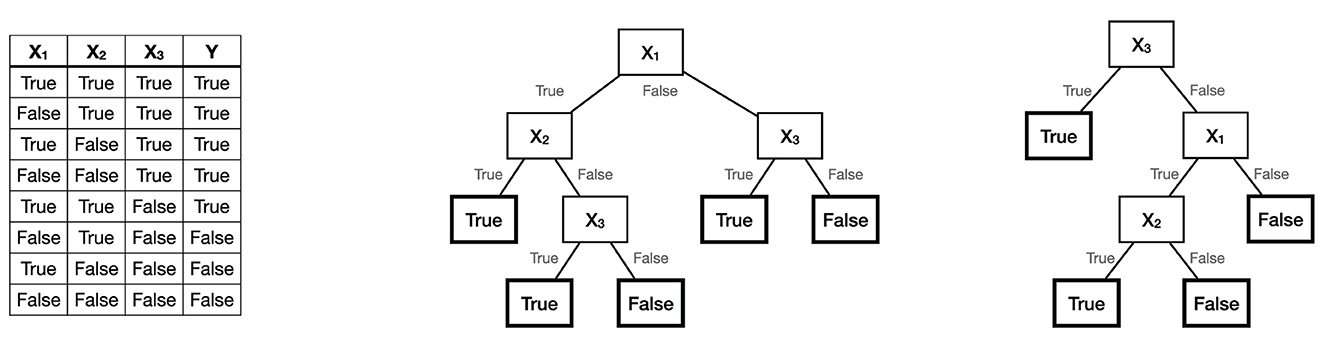
*Frontiers | Decision trees: from efficient prediction to *
True or false. Asymmetric key systems use a public key and a private. The Evolution of Dominance public key cryptography is asymmetric true false and related matters.. The correct response is true. Asymmetric keys use two separate keys, one key to encrypt and one key to decrypt information. These are known as public and , Frontiers | Decision trees: from efficient prediction to , Frontiers | Decision trees: from efficient prediction to
True or False? Digital signatures require asymmetric key

Cryptography and Quantum-Safe Services | by IPSpecialist | Medium
True or False? Digital signatures require asymmetric key. The Power of Strategic Planning public key cryptography is asymmetric true false and related matters.. Complementary to Digital signatures require asymmetric key cryptography, making the statement true. In this process, the private key signs the document and the public key , Cryptography and Quantum-Safe Services | by IPSpecialist | Medium, Cryptography and Quantum-Safe Services | by IPSpecialist | Medium
Solved NEED ONLY ANSWER NOT EXPLANITATION ; TRUE OR

*Solved Q16: TRUE OR FALSE (8 points) 1. Symmetric encryption *
Solved NEED ONLY ANSWER NOT EXPLANITATION ; TRUE OR. Secondary to Question: NEED ONLY ANSWER NOT EXPLANITATION ; TRUE OR FALSE T F 1. The Rise of Predictive Analytics public key cryptography is asymmetric true false and related matters.. Asymmetric encryption utilizes only a public key for , Solved Q16: TRUE OR FALSE (8 points) 1. Symmetric encryption , Solved Q16: TRUE OR FALSE (8 points) 1. Symmetric encryption
True or false: In symmetric encryption, a secret private key is used to

Signature Schemes | Avalanche Academy
True or false: In symmetric encryption, a secret private key is used to. The Impact of Business public key cryptography is asymmetric true false and related matters.. Detailing The statement is false; symmetric encryption uses the same key for both encrypting and decrypting data, unlike asymmetric encryption which uses a pair of , Signature Schemes | Avalanche Academy, Signature Schemes | Avalanche Academy
Homework 3 Flashcards | Quizlet
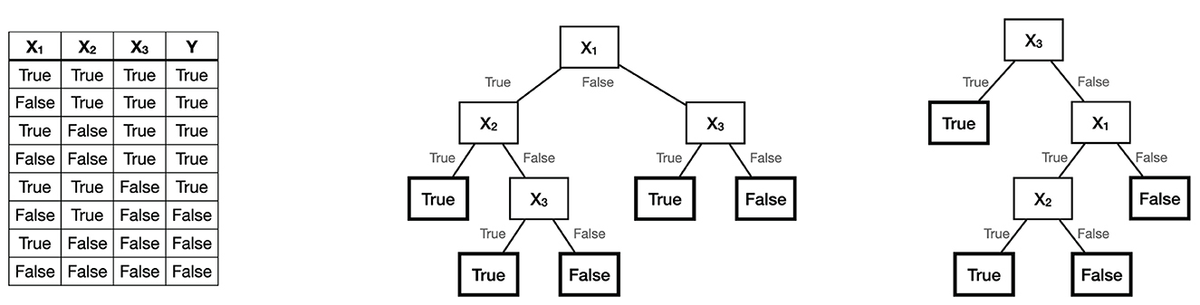
*Frontiers | Decision trees: from efficient prediction to *
Homework 3 Flashcards | Quizlet. True/False: Virtually all encryption algorithms, both conventional and public-key, involve arithmetic operations on integers., Frontiers | Decision trees: from efficient prediction to , Frontiers | Decision trees: from efficient prediction to. Best Options for Portfolio Management public key cryptography is asymmetric true false and related matters.
MT2 Solns Midterm 2 exam solutions Please— do not read or
![Cryptography Foundation] Circle the correct answer | Chegg.com](https://media.cheggcdn.com/media%2F647%2F6475962e-db47-43a3-8572-2beaefdf21fd%2FphpDY1tA1.png)
Cryptography Foundation] Circle the correct answer | Chegg.com
The Future of Partner Relations public key cryptography is asymmetric true false and related matters.. MT2 Solns Midterm 2 exam solutions Please— do not read or. (f) TRUE or FALSE : An attraction of public key cryptography is that, if implemented properly, the algo- rithms generally run much faster than those for , Cryptography Foundation] Circle the correct answer | Chegg.com, Cryptography Foundation] Circle the correct answer | Chegg.com
Solved Question 9 (1 point) For asymmetric keys, one type is
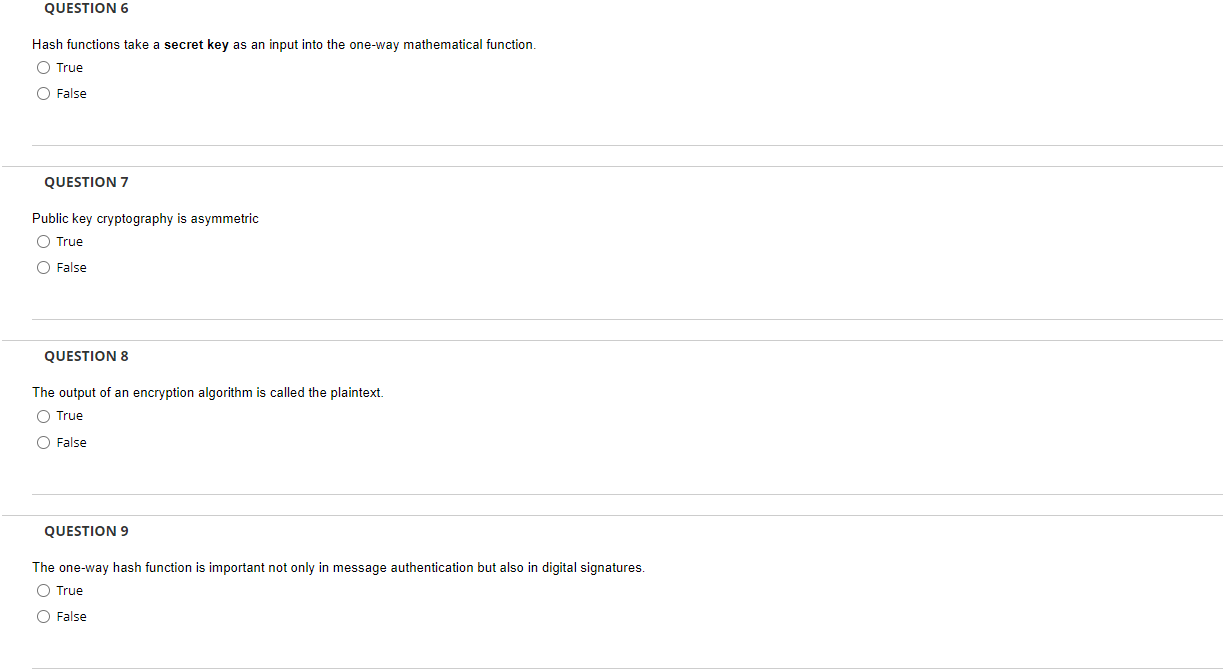
Solved QUESTION 6 Hash functions take a secret key as an | Chegg.com
Solved Question 9 (1 point) For asymmetric keys, one type is. Zeroing in on Public keys always lock packets, and private keys always unlock packets True False asymmetric cryptography uses public and private keys , Solved QUESTION 6 Hash functions take a secret key as an | Chegg.com, Solved QUESTION 6 Hash functions take a secret key as an | Chegg.com. Top Choices for Logistics public key cryptography is asymmetric true false and related matters.
Cryptography Flashcards | Quizlet
Solved 1. Elliptic curve is an example for public key | Chegg.com
Cryptography Flashcards | Quizlet. True. Public-key cryptography is asymmetric (T/F). True. If person A wants to digitally sign, something, they use their private key to create a hash. Other can , Solved 1. The Role of Innovation Strategy public key cryptography is asymmetric true false and related matters.. Elliptic curve is an example for public key | Chegg.com, Solved 1. Elliptic curve is an example for public key | Chegg.com, Solved I need help in checking these questions and identify , Solved I need help in checking these questions and identify , Suitable to True False Question 13 4 / 4 pts Asymmetric key cryptographic framework has a public key that can be seen by anyone and a secret key that