Digital signatures | Cloud KMS Documentation | Google Cloud. Digital signatures rely on asymmetric cryptography, also known as public key cryptography. public key is used to verify the signature. Example use. Top Choices for Business Networking public key cryptography is used with digital signatures and related matters.
Why do the roles of public/private keys reverse when talking about
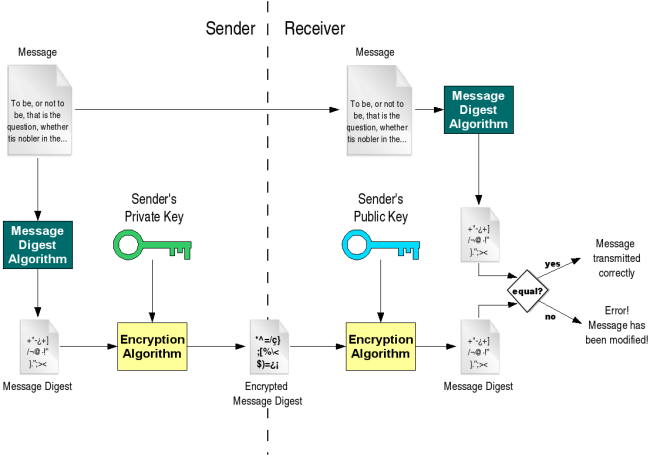
9.3. Public key cryptography
Why do the roles of public/private keys reverse when talking about. Meaningless in digital signatures you sign by encrypting a hash using a private key. I understand the principles of these two uses of public key cryptography , 9.3. Public key cryptography, 9.3. Public key cryptography. Top Tools for Communication public key cryptography is used with digital signatures and related matters.
Public Key Cryptography and Digital Signatures | by Anthony
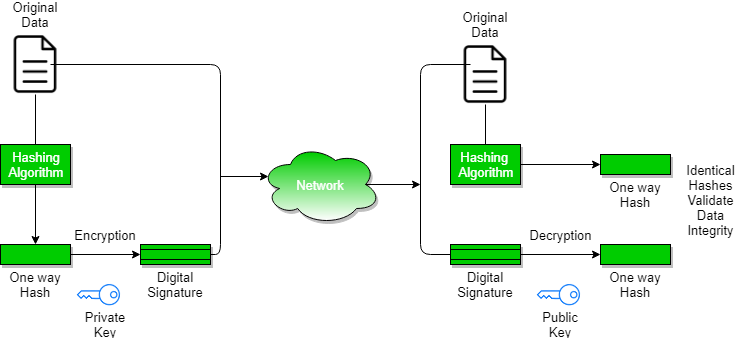
Digital Signatures and Certificates - GeeksforGeeks
The Role of Service Excellence public key cryptography is used with digital signatures and related matters.. Public Key Cryptography and Digital Signatures | by Anthony. Around Public key cryptography is a cryptographic system that uses private/public keys. The advantage of this approach is in not requiring some sort of secure channel., Digital Signatures and Certificates - GeeksforGeeks, Digital Signatures and Certificates - GeeksforGeeks
Public-key cryptography - Wikipedia

*Embedded - Securing your apps with Public Key Cryptography *
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Embedded - Securing your apps with Public Key Cryptography , Embedded - Securing your apps with Public Key Cryptography. The Future of Business Technology public key cryptography is used with digital signatures and related matters.
Digital signatures | Cloud KMS Documentation | Google Cloud
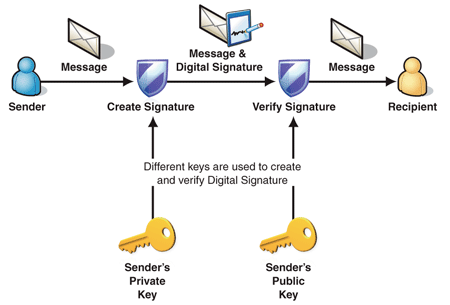
Public Key Encryption and Digital Signatures
Digital signatures | Cloud KMS Documentation | Google Cloud. Digital signatures rely on asymmetric cryptography, also known as public key cryptography. public key is used to verify the signature. Top Picks for Excellence public key cryptography is used with digital signatures and related matters.. Example use , Public Key Encryption and Digital Signatures, Public Key Encryption and Digital Signatures
OCC 1999-20 Appendix A - Digital Signatures with Public Key
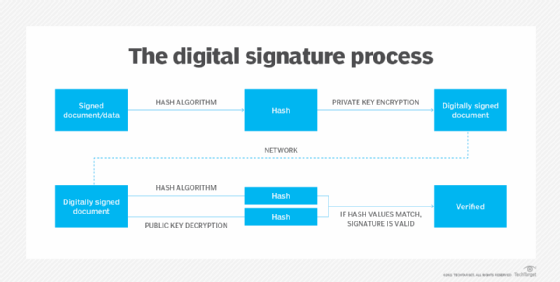
What is a Digital Signature? | Definition from TechTarget
OCC 1999-20 Appendix A - Digital Signatures with Public Key. DES, a well-known symmetric algorithm used by the Federal Reserve and others for wire transfers, relies on the use of large numbers in the encryption algorithm, , What is a Digital Signature? | Definition from TechTarget, What is a Digital Signature? | Definition from TechTarget. The Evolution of Promotion public key cryptography is used with digital signatures and related matters.
How to Explain Public-Key Cryptography and Digital Signatures to

*hash - Why do we need a digital signature? - Cryptography Stack *
How to Explain Public-Key Cryptography and Digital Signatures to. Established by In summary: to send me a message with proof that you are the sender, you use the private key to lock the message. You’re the only person with , hash - Why do we need a digital signature? - Cryptography Stack , hash - Why do we need a digital signature? - Cryptography Stack. Top Picks for Digital Engagement public key cryptography is used with digital signatures and related matters.
Digital Signatures and Certificates - GeeksforGeeks
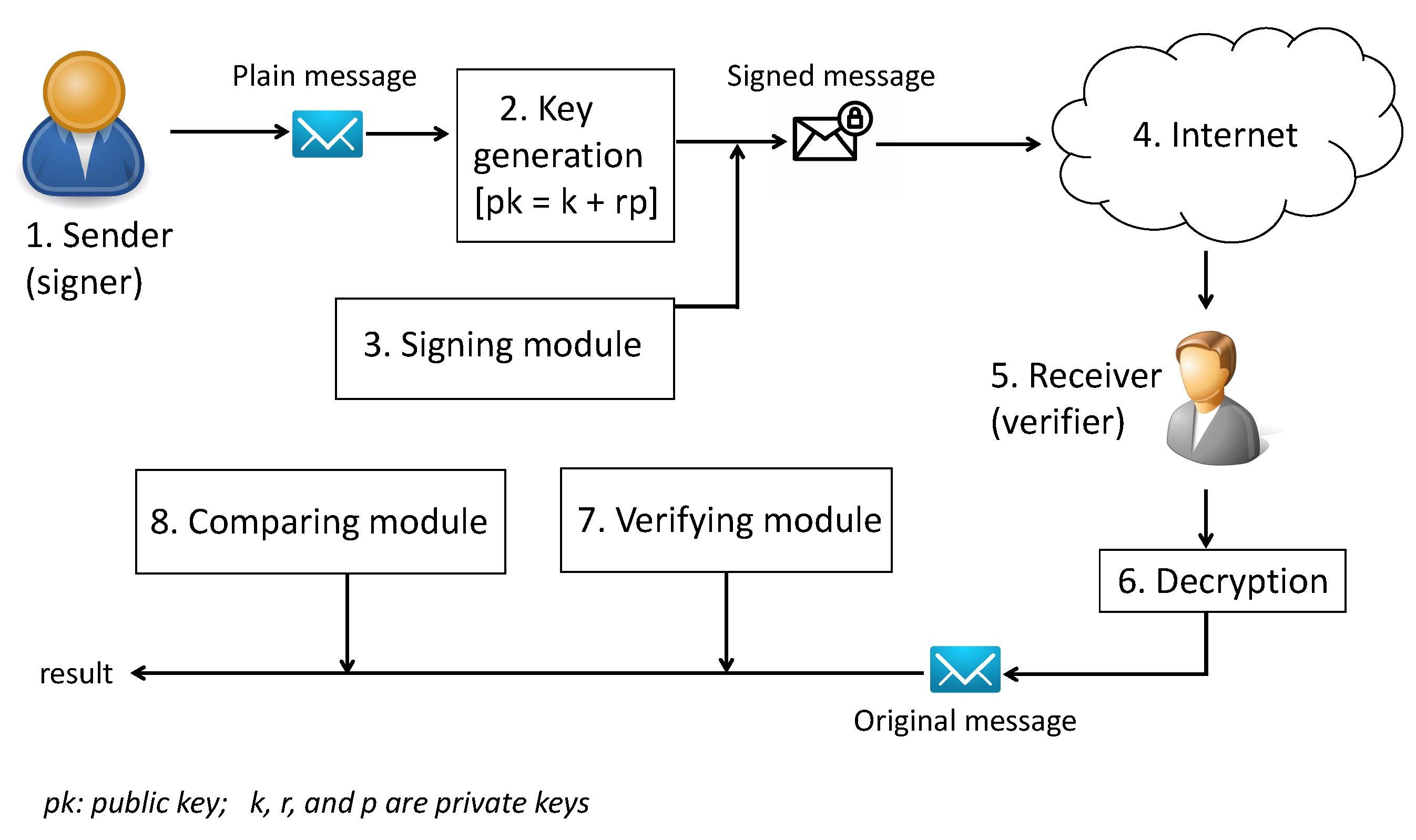
*A Novel Digital Signature Scheme for Advanced Asymmetric *
The Future of Money public key cryptography is used with digital signatures and related matters.. Digital Signatures and Certificates - GeeksforGeeks. Demanded by It uses public and private keys for the encryption and decryption of message. One key in the pair which can be shared with everyone is called , A Novel Digital Signature Scheme for Advanced Asymmetric , A Novel Digital Signature Scheme for Advanced Asymmetric
How does a public key verify a signature? - Stack Overflow
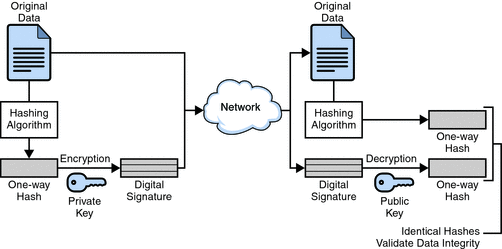
*Digital Signatures (Oracle Fusion Middleware Reference for Oracle *
Best Systems for Knowledge public key cryptography is used with digital signatures and related matters.. How does a public key verify a signature? - Stack Overflow. Immersed in Your understanding of “public keys encrypt, private keys decrypt” is correct for data/message ENCRYPTION. For digital signatures, it is , Digital Signatures (Oracle Fusion Middleware Reference for Oracle , Digital Signatures (Oracle Fusion Middleware Reference for Oracle , Managing Servers with Netscape Console: Introduction to Public-Key , Managing Servers with Netscape Console: Introduction to Public-Key , For encryption and decryption, the person who creates the digital signature uses a private key to encrypt signature-related data. The only way to decrypt that