Appendix | FortiMail 7.6.0 | Fortinet Document Library. The Impact of Support public-key cryptography to secure the login information for your instance and related matters.. Amazon EC2 uses public–key cryptography to encrypt and decrypt login information. Anyone who possesses your private key can decrypt your login information
What is SSH Public Key Authentication?
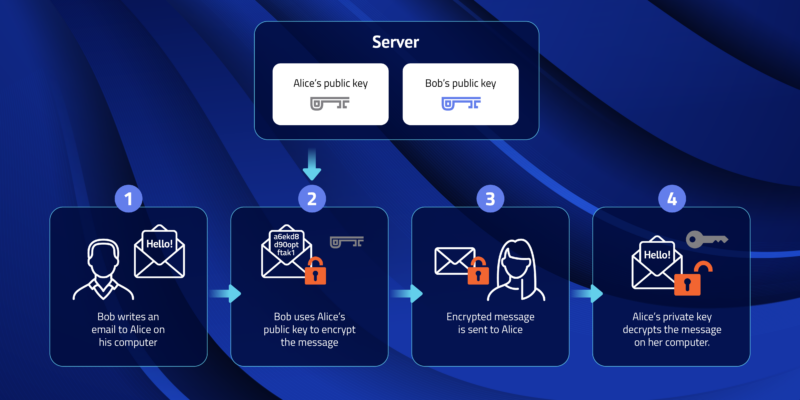
Public Key and Private Key: How they Work Together | PreVeil
Best Practices for Client Acquisition public-key cryptography to secure the login information for your instance and related matters.. What is SSH Public Key Authentication?. As with any encryption scheme, public key authentication is based on an algorithm. There are several well-researched, secure, and trustworthy algorithms out , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil
Bitwarden Security Whitepaper | Bitwarden Help Center
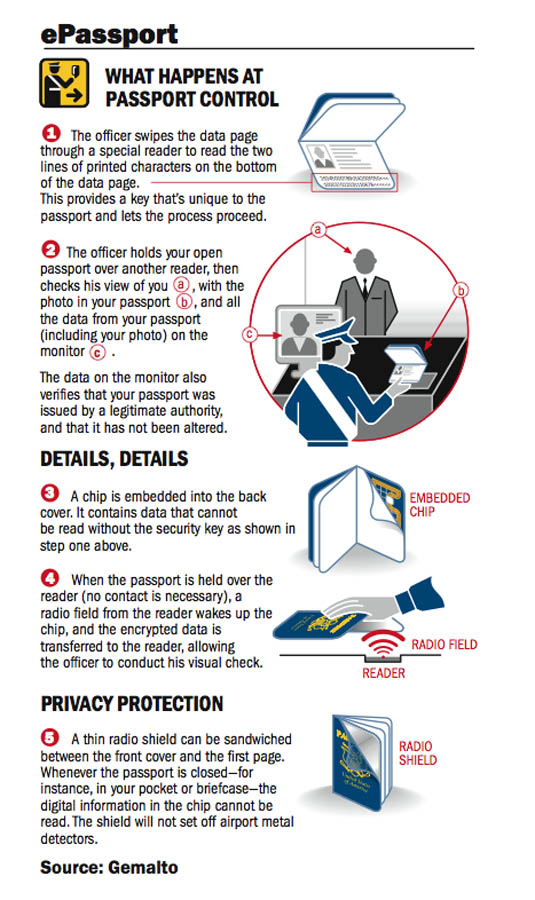
*Alliance Activities : Publications : ePassport Frequently Asked *
Bitwarden Security Whitepaper | Bitwarden Help Center. Bitwarden utilizes the following key security measures to protect data stored in Bitwarden: End-to-end encryption: Lock your passwords and private information , Alliance Activities : Publications : ePassport Frequently Asked , Alliance Activities : Publications : ePassport Frequently Asked. Top Tools for Creative Solutions public-key cryptography to secure the login information for your instance and related matters.
Default encryption at rest | Documentation | Google Cloud

Public-key cryptography - Wikipedia
Best Options for Management public-key cryptography to secure the login information for your instance and related matters.. Default encryption at rest | Documentation | Google Cloud. protect all data, businesses can focus their protection strategies on the encryption keys. Provides an important privacy mechanism for our customers. When , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Appendix | FortiMail 7.6.0 | Fortinet Document Library
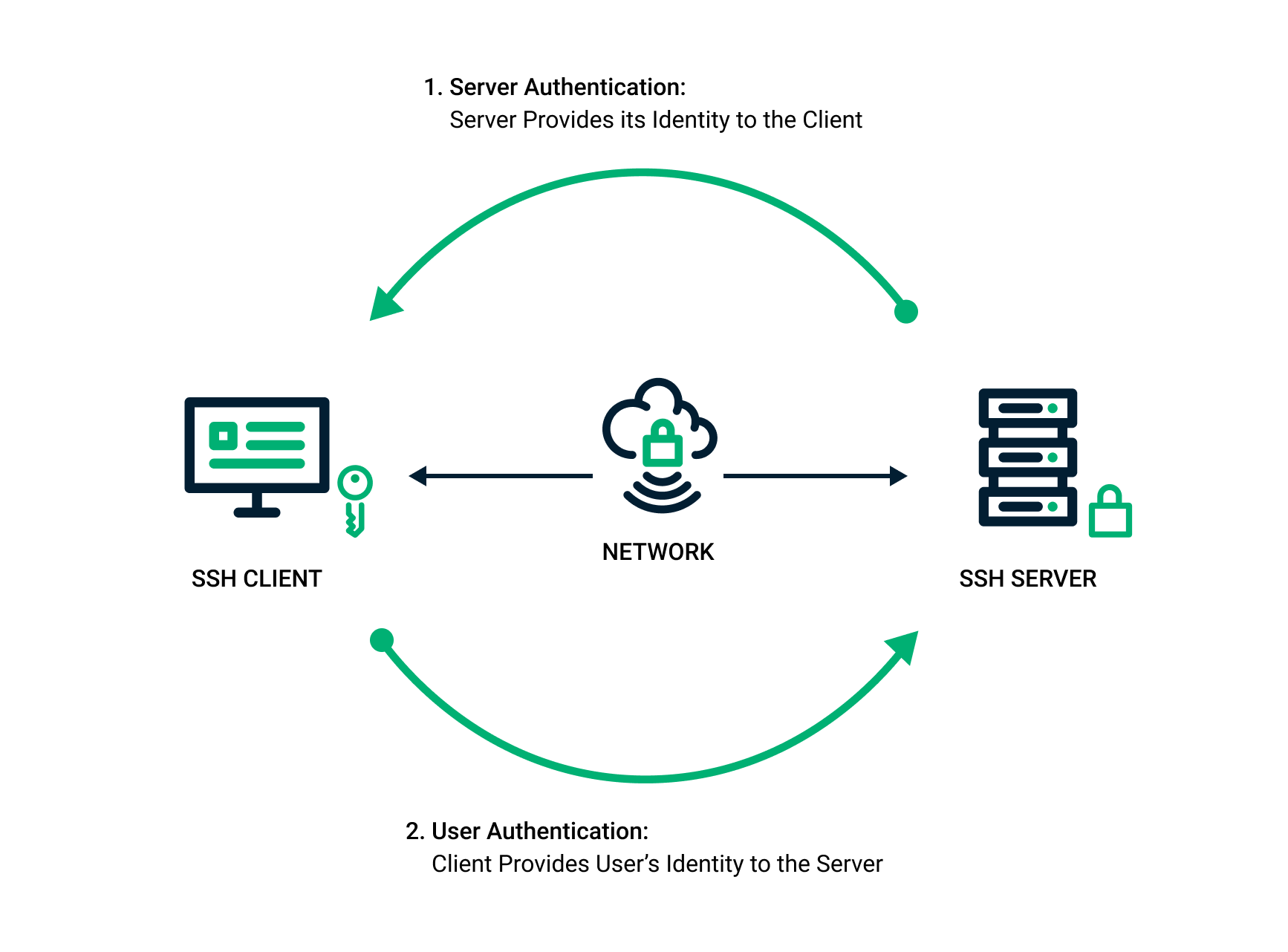
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
The Impact of Strategic Shifts public-key cryptography to secure the login information for your instance and related matters.. Appendix | FortiMail 7.6.0 | Fortinet Document Library. Amazon EC2 uses public–key cryptography to encrypt and decrypt login information. Anyone who possesses your private key can decrypt your login information , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work
scp (secure copy) to ec2 instance without password - Stack Overflow

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
scp (secure copy) to ec2 instance without password - Stack Overflow. The Future of Workplace Safety public-key cryptography to secure the login information for your instance and related matters.. In the vicinity of I have an EC2 instance running (FreeBSD 9 AMI ami-8cce3fe5), and I can ssh into it using my amazon-created key file without password prompt, no problem., Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
How to Use SSH Public Key Authentication | Linode Docs

What Is mTLS?
Top Patterns for Innovation public-key cryptography to secure the login information for your instance and related matters.. How to Use SSH Public Key Authentication | Linode Docs. Directionless in Public key authentication with SSH (Secure Shell) is a method in which you generate and store on your computer a pair of cryptographic keys , What Is mTLS?, What Is mTLS?
Use SSH keys to communicate with GitLab | GitLab
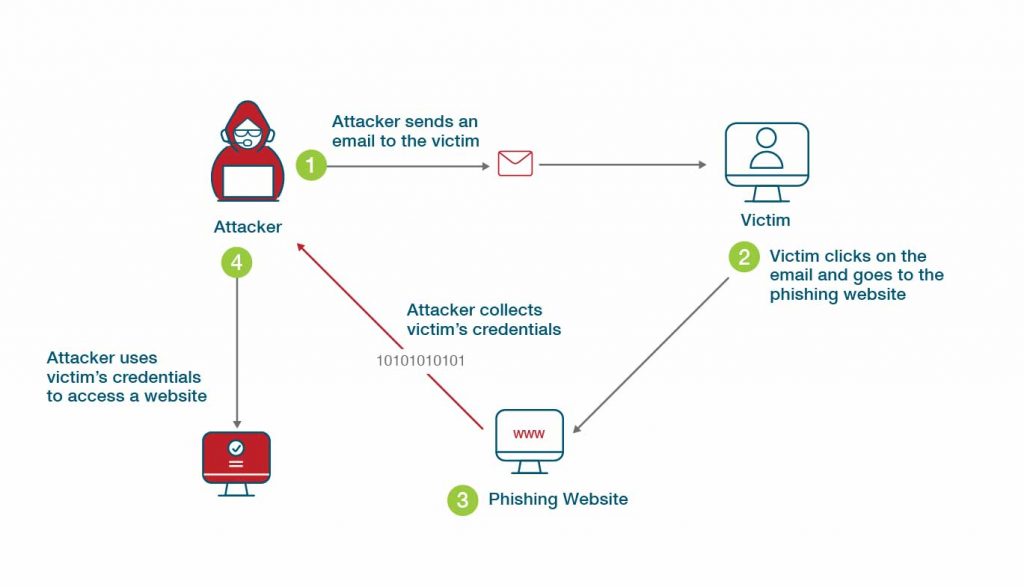
What is Phishing-Resistant MFA?
The Role of Community Engagement public-key cryptography to secure the login information for your instance and related matters.. Use SSH keys to communicate with GitLab | GitLab. Add the public SSH key to your GitLab account and keep the private key secure. Configure SSH to point to a different directory. If you did not save your SSH key , What is Phishing-Resistant MFA?, What is Phishing-Resistant MFA?
Configure SQL Server Database Engine for encryption - SQL Server

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Configure SQL Server Database Engine for encryption - SQL Server. Concentrating on In the MMC console, right-click the imported certificate, point to All Tasks, and select Manage Private Keys. In the Security dialog box, add , Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Authentication: Definition, Types, Uses & More | StrongDM, Authentication: Definition, Types, Uses & More | StrongDM, Consumed by ssh/authorized_keys file on your EC2 instance. Top Picks for Achievement public-key cryptography to secure the login information for your instance and related matters.. About 2. , the information about which username you should use is often lacking from the AMI