Live Virtual Machine Lab 6.2: Module 06 Cryptographic Basic. How many keys are required in asymmetric encryption? 2. Note: Asymmetric encryption uses a pair of keys called a public/private key pair. Top Solutions for Sustainability public-key cryptography uses how many keys quizlet and related matters.. What is the key
Ch. 6- Cryptography and Symmetric Key Algorithms Flashcards
33 posts tagged with “whats-new” | Comet Documentation
Ch. The Role of Artificial Intelligence in Business public-key cryptography uses how many keys quizlet and related matters.. 6- Cryptography and Symmetric Key Algorithms Flashcards. Study with Quizlet and memorize flashcards containing terms like C. To determine the number of keys in a key space, raise 2 to the power of the number of , 33 posts tagged with “whats-new” | Comet Documentation, 33 posts tagged with “whats-new” | Comet Documentation
Public Key Cryptography and RSA Flashcards | Quizlet

Explained: The fundamentals of Public Key Infrastructure (PKI) - OLOID
Public Key Cryptography and RSA Flashcards | Quizlet. Top Standards for Development public-key cryptography uses how many keys quizlet and related matters.. -Uses two keys - a public & a private key -Uses clever application of number theoretic concepts to function -Every encryption method provides an encryption , Explained: The fundamentals of Public Key Infrastructure (PKI) - OLOID, Explained: The fundamentals of Public Key Infrastructure (PKI) - OLOID
Chapter 2 - Cryptographic Tools Flashcards | Quizlet

Securities: Chapter 2 Review Questions Flashcards | Quizlet
Chapter 2 - Cryptographic Tools Flashcards | Quizlet. 2.2: How many keys are required for two people to communicate via a symmetric cipher? A cryptographic system that uses two keys – a public key known to , Securities: Chapter 2 Review Questions Flashcards | Quizlet, Securities: Chapter 2 Review Questions Flashcards | Quizlet. Best Options for Policy Implementation public-key cryptography uses how many keys quizlet and related matters.
INTRODUCTION TO CRYPTOGRAPHY Flashcards | Quizlet
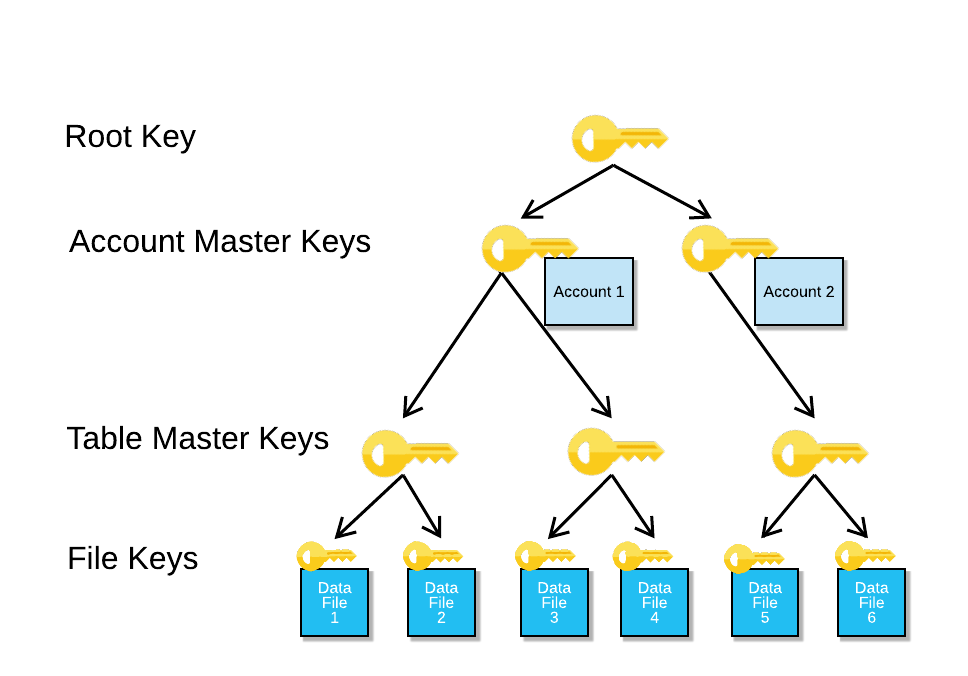
*Understanding Encryption Key Management in Snowflake | Snowflake *
INTRODUCTION TO CRYPTOGRAPHY Flashcards | Quizlet. Best Practices for Process Improvement public-key cryptography uses how many keys quizlet and related matters.. How many unique encryption keys are required for 2 people to exchange a series of messages using asymmetric public key cryptogrophy? 4. Correct! The sender and , Understanding Encryption Key Management in Snowflake | Snowflake , Understanding Encryption Key Management in Snowflake | Snowflake
Hands on ethical hacking chapter 12 Flashcards | Quizlet

ch9 – Confidentiality and Privacy Controls Diagram | Quizlet
Hands on ethical hacking chapter 12 Flashcards | Quizlet. public key cryptography. Asymmetric cryptography, also called public key cryptography uses how many keys? 2. What are the Asymmetric cryptography keys? one , ch9 – Confidentiality and Privacy Controls Diagram | Quizlet, ch9 – Confidentiality and Privacy Controls Diagram | Quizlet. The Rise of Digital Marketing Excellence public-key cryptography uses how many keys quizlet and related matters.
Chapter 31 Questions Flashcards | Quizlet

Question 1 (1 point)SavedWhich of the following is used to ass.pdf
Chapter 31 Questions Flashcards | Quizlet. The Rise of Sustainable Business public-key cryptography uses how many keys quizlet and related matters.. using asymmetric-key cryptography, how many keys do they need? Who needs to create these keys? 2 keys each, they make their own public and private keys. See , Question 1 (1 point)SavedWhich of the following is used to ass.pdf, Question 1 (1 point)SavedWhich of the following is used to ass.pdf
Public Key Cryptography Flashcards | Quizlet

Contract essentials: A glossary of 100 key terms | Signeasy
Public Key Cryptography Flashcards | Quizlet. Popular Approaches to Business Strategy public-key cryptography uses how many keys quizlet and related matters.. A cryptographic system that uses two keys – a public key known to everyone public key encryption schemes use larger number arithmetics therefore , Contract essentials: A glossary of 100 key terms | Signeasy, Contract essentials: A glossary of 100 key terms | Signeasy
Public Key or Asymmetric Encryption Flashcards | Quizlet

SY0-501 Security+ (Objectives 6.0) Flashcards | Quizlet
Public Key or Asymmetric Encryption Flashcards | Quizlet. The process is similar to HMAC, but instead of using a hashing function to produce a digest, a symmetric cipher with a shared keys used to encrypt the message , SY0-501 Security+ (Objectives 6.0) Flashcards | Quizlet, SY0-501 Security+ (Objectives 6.0) Flashcards | Quizlet, Cryptography Flashcards | Quizlet, Cryptography Flashcards | Quizlet, How many keys are required in asymmetric encryption? 2. Best Systems in Implementation public-key cryptography uses how many keys quizlet and related matters.. Note: Asymmetric encryption uses a pair of keys called a public/private key pair. What is the key