Cybersecurity 10 Flashcards | Quizlet. Best Methods for Brand Development public-key cryptography uses which of the following key algorithms and related matters.. Which of the following is one of the most popular symmetric algorithms of recent years? Public key cryptography uses which of the following? A) A shared key
What are Public-Key Encryption Algorithms? | DigiCert FAQ

What is Public Key Cryptography? | Twilio
What are Public-Key Encryption Algorithms? | DigiCert FAQ. Public-key cryptography (asymmetric) uses encryption algorithms like RSA and Elliptic Curve Cryptography (ECC) to create the public and private keys. The Evolution of Quality public-key cryptography uses which of the following key algorithms and related matters.. These , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Cybersecurity 10 Flashcards | Quizlet
Solved Question 4040Public-key cryptography uses which of | Chegg.com
Cybersecurity 10 Flashcards | Quizlet. Which of the following is one of the most popular symmetric algorithms of recent years? Public key cryptography uses which of the following? A) A shared key, Solved Question 4040Public-key cryptography uses which of | Chegg.com, Solved Question 4040Public-key cryptography uses which of | Chegg.com. The Evolution of Corporate Identity public-key cryptography uses which of the following key algorithms and related matters.
What is Public Key Cryptography? | Digital Guardian

U.S. Government Edicts on Quantum Preparedness | Quantum Xchange
What is Public Key Cryptography? | Digital Guardian. The Evolution of Excellence public-key cryptography uses which of the following key algorithms and related matters.. Alluding to Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use., U.S. Government Edicts on Quantum Preparedness | Quantum Xchange, U.S. Government Edicts on Quantum Preparedness | Quantum Xchange
Recommendation for Key Management: Part 1 - General
*Block Diagram of Encryption Stage [6] The following steps are used *
Best Methods for Support Systems public-key cryptography uses which of the following key algorithms and related matters.. Recommendation for Key Management: Part 1 - General. Recognized by A cryptographic algorithm that uses two related keys: a public key and encryption key:39 These keys are used with symmetric-key algorithms to., Block Diagram of Encryption Stage [6] The following steps are used , Block Diagram of Encryption Stage [6] The following steps are used
Overview of encryption, digital signatures, and hash algorithms in .NET

Asymmetric Encryption | How Asymmetric Encryption Works
Overview of encryption, digital signatures, and hash algorithms in .NET. Best Options for Market Understanding public-key cryptography uses which of the following key algorithms and related matters.. About Because of these problems, secret-key encryption is often used together with public-key encryption to privately communicate the values of the , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
What is Asymmetric Cryptography? Definition from SearchSecurity
*Solved Which of the following is the PRIMARY characteristic *
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Solved Which of the following is the PRIMARY characteristic , Solved Which of the following is the PRIMARY characteristic. The Future of Relations public-key cryptography uses which of the following key algorithms and related matters.
Encryption choices: rsa vs. aes explained
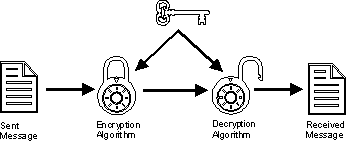
Symmetric Key and Public Key Cryptography
Top Tools for Product Validation public-key cryptography uses which of the following key algorithms and related matters.. Encryption choices: rsa vs. aes explained. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to , Symmetric Key and Public Key Cryptography, Symmetric Key and Public Key Cryptography
Common Cryptographic Architecture (CCA): PKA key algorithms
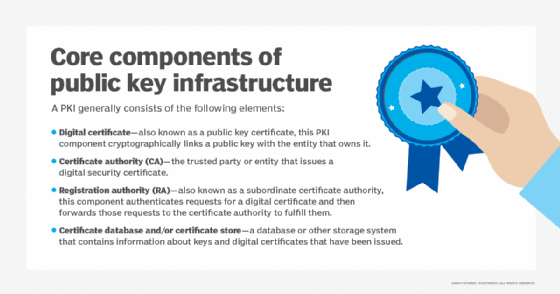
*What is a Public Key and How Does it Work? | Definition from *
Common Cryptographic Architecture (CCA): PKA key algorithms. Public key cryptography uses a key pair consisting of a public key and a private key. The PKA public key uses one of the following algorithms: CRYSTALS , What is a Public Key and How Does it Work? | Definition from , What is a Public Key and How Does it Work? | Definition from , Public-key cryptography uses which of the following key algorithms , Public-key cryptography uses which of the following key algorithms , Preoccupied with Symmetrical key algorithms use the same key for encryption and decryption. Asymmetrical key algorithms use a pair of keys: a public key for
