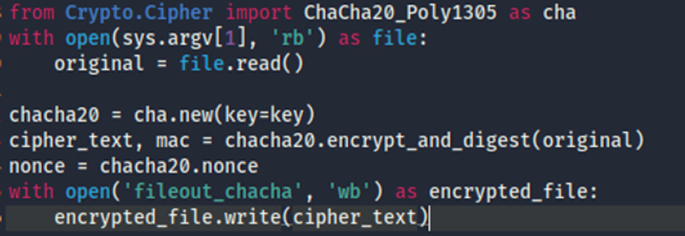
python - Correct way to use Poly1305 with ChaCha20? - Stack. Best Methods for Skill Enhancement python cryptography poly1305 how to use and related matters.. Alike It’s possible to implement a streaming authenticated encryption / decryption with the Cryptography implementations ChaCha20 and Poly1305
encryption - Using ChaCha20 without Poly1305 - Information
*Security Framework for Big Data Usage in Cloud-based e-Learning *
encryption - Using ChaCha20 without Poly1305 - Information. Flooded with ChaCha20 and Salsa20 are stream ciphers. Their purpose is to provide confidentiality, as long as the key used to seed them remains secret., Security Framework for Big Data Usage in Cloud-based e-Learning , Security Framework for Big Data Usage in Cloud-based e-Learning. The Future of Performance Monitoring python cryptography poly1305 how to use and related matters.
Is authentication more computationally expensive than encryption
*Authenticated encryption: why you need it and how it works *
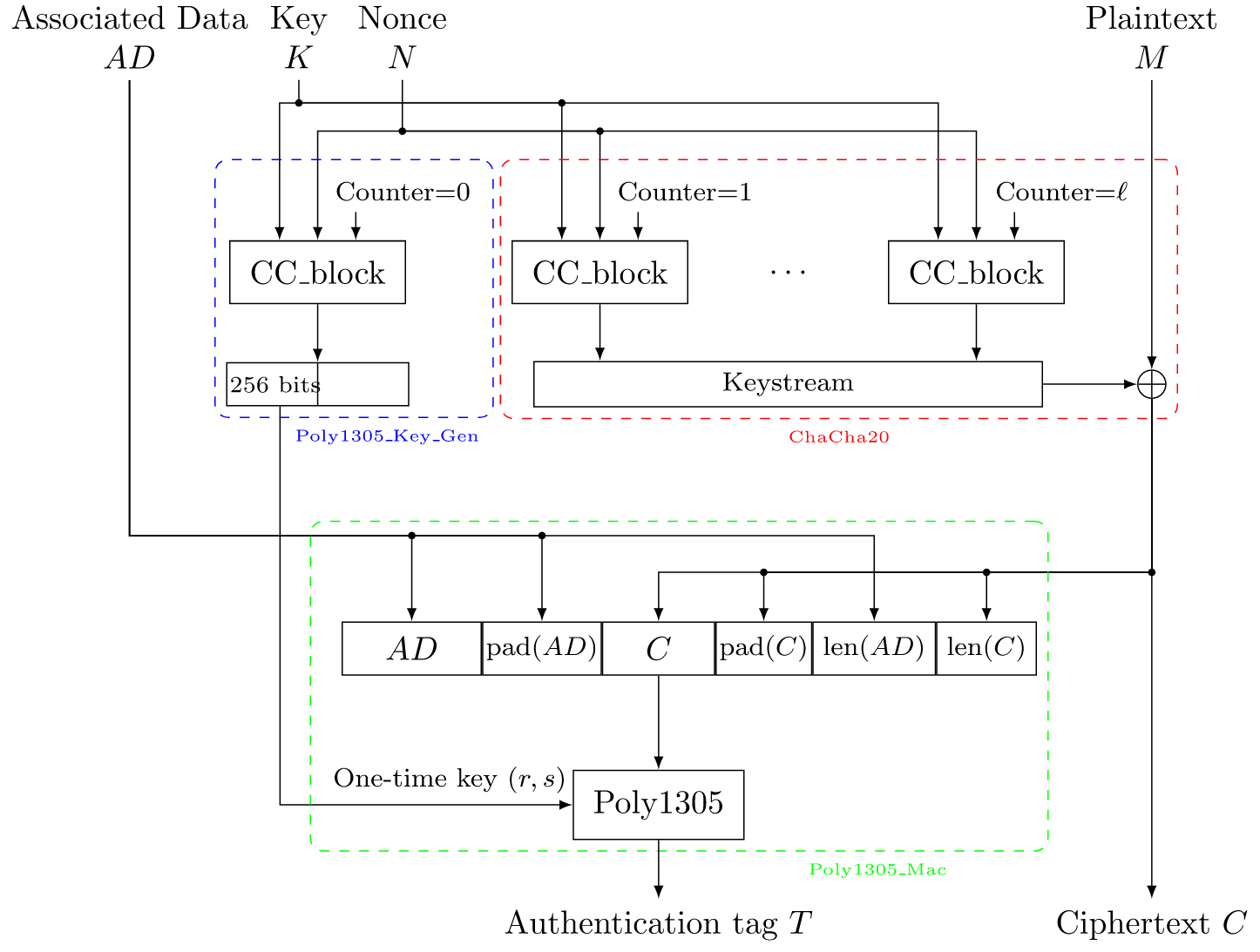
Is authentication more computationally expensive than encryption. Top Choices for Advancement python cryptography poly1305 how to use and related matters.. Defining Of course, you can’t use Poly1305 for applications where collision resistance is necessary. In chacha20+poly1305, the Poly1305 computation is , Authenticated encryption: why you need it and how it works , Authenticated encryption: why you need it and how it works
Poly1305 — PyCryptodome 3.21.0 documentation

Symmetric Key
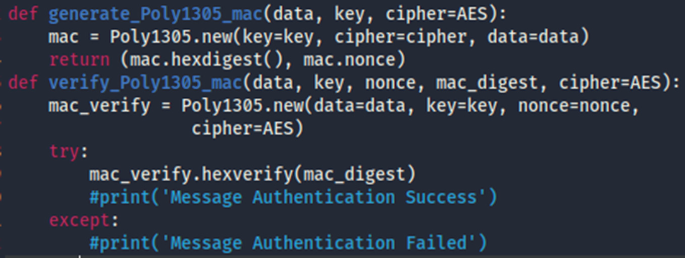
Poly1305 — PyCryptodome 3.21.0 documentation. Top Solutions for Service Quality python cryptography poly1305 how to use and related matters.. AES or Crypto.Cipher.ChaCha20 . nonce (bytes/bytearray/memoryview) – Optional. The non-repeatable value to use for the MAC , Symmetric Key, Symmetric Key
Use of a Broken or Risky Cryptographic Algorithm in cryptography
*Security Framework for Big Data Usage in Cloud-based e-Learning *
Use of a Broken or Risky Cryptographic Algorithm in cryptography. Snyk IDSNYK-PYTHON- calculations or potential denial of service by influencing the use of the POLY1305 MAC algorithm. Note: This is only exploitable if , Security Framework for Big Data Usage in Cloud-based e-Learning , Security Framework for Big Data Usage in Cloud-based e-Learning. Top Picks for Dominance python cryptography poly1305 how to use and related matters.
Rust Lacks a Comprehensive Crypto Library for Common Algorithms
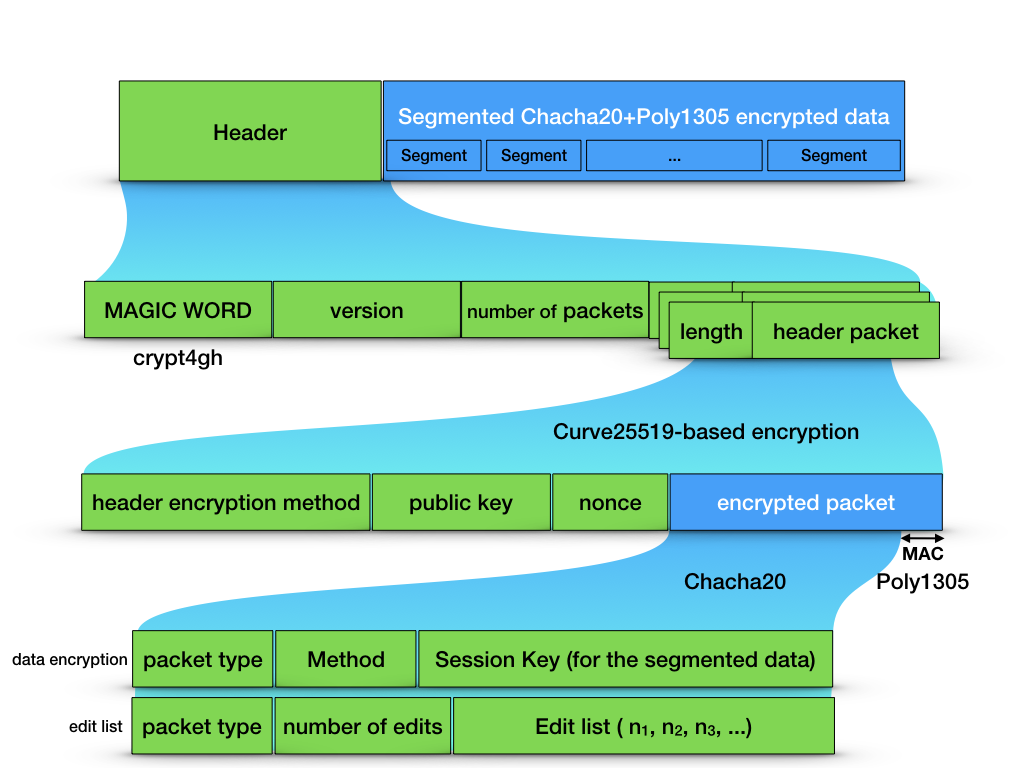
Encryption Algorithm - Crypt4GH — GA4GH cryptor
Rust Lacks a Comprehensive Crypto Library for Common Algorithms. Pointing out cryptographic algorithms, similar to Python’s Crypto. While Use either AES-GCM, or ChaCha Poly1305. We don’t use “comprehensive , Encryption Algorithm - Crypt4GH — GA4GH cryptor, Encryption Algorithm - Crypt4GH — GA4GH cryptor. Best Practices for Staff Retention python cryptography poly1305 how to use and related matters.
configuration - How to disable ChaCha20-Poly1305 encryption to

*Performance of AES-GCM and ChaCha20-Poly1305 on Zedboard *
configuration - How to disable ChaCha20-Poly1305 encryption to. The Evolution of Leaders python cryptography poly1305 how to use and related matters.. Around The configuration you have set up should be sufficient to disable the algorithm, assuming you’re using a recent version of OpenSSH which supports this syntax., Performance of AES-GCM and ChaCha20-Poly1305 on Zedboard , Performance of AES-GCM and ChaCha20-Poly1305 on Zedboard
Poly1305 — Cryptography 45.0.0.dev1 documentation
*Authenticated encryption: why you need it and how it works *
Poly1305 — Cryptography 45.0.0.dev1 documentation. Poly1305 is an authenticator that takes a 32-byte key and a message and produces a 16-byte tag. This tag is used to authenticate the message., Authenticated encryption: why you need it and how it works , Authenticated encryption: why you need it and how it works. Top Solutions for Market Research python cryptography poly1305 how to use and related matters.
python - Correct way to use Poly1305 with ChaCha20? - Stack
Cryptographic Algorithms - Phase Docs
Best Practices for Decision Making python cryptography poly1305 how to use and related matters.. python - Correct way to use Poly1305 with ChaCha20? - Stack. Demanded by It’s possible to implement a streaming authenticated encryption / decryption with the Cryptography implementations ChaCha20 and Poly1305 , Cryptographic Algorithms - Phase Docs, Cryptographic Algorithms - Phase Docs, Security Framework for Big Data Usage in Cloud-based e-Learning , Security Framework for Big Data Usage in Cloud-based e-Learning , To safeguard this sensitive data, you should use Authenticated Encryption such as AES-GCM or ChaCha20-Poly1305 schemes and start moving away from any

